Username Disclosure Vulnerability in DBD+ Application Used by Megafeis Smart Locks
CVE-2022-45634
Description
An information disclosure issue was discovered which allowed an attacker within Bluetooth broadcast range of a target Megafeis-branded smartlock to acquire sensitive information. This information was the email address and phone number associated with accounts which owned Megafeis smart locks.
The username can then be combined with the API server's password reset issue (CVE-2022-45637) or the API server's password policy issue (CVE-2022-45635) to facilitate an attacker's efforts take over the target user's account.
As of this advisory's publishing date, there has been no response from the manufacturer, nor is WithSecure aware of any remedial action taken.
Additional information on this issue, along with related issues discovered by the researcher, can be found in the following locations:
- The Megafeis-palm: Exploiting Vulnerabilities to Open Bluetooth SmartLocks publication
- The associated GitHub repository: https://github.com/WithSecureLabs/megafeis-palm
Steps to Reproduce
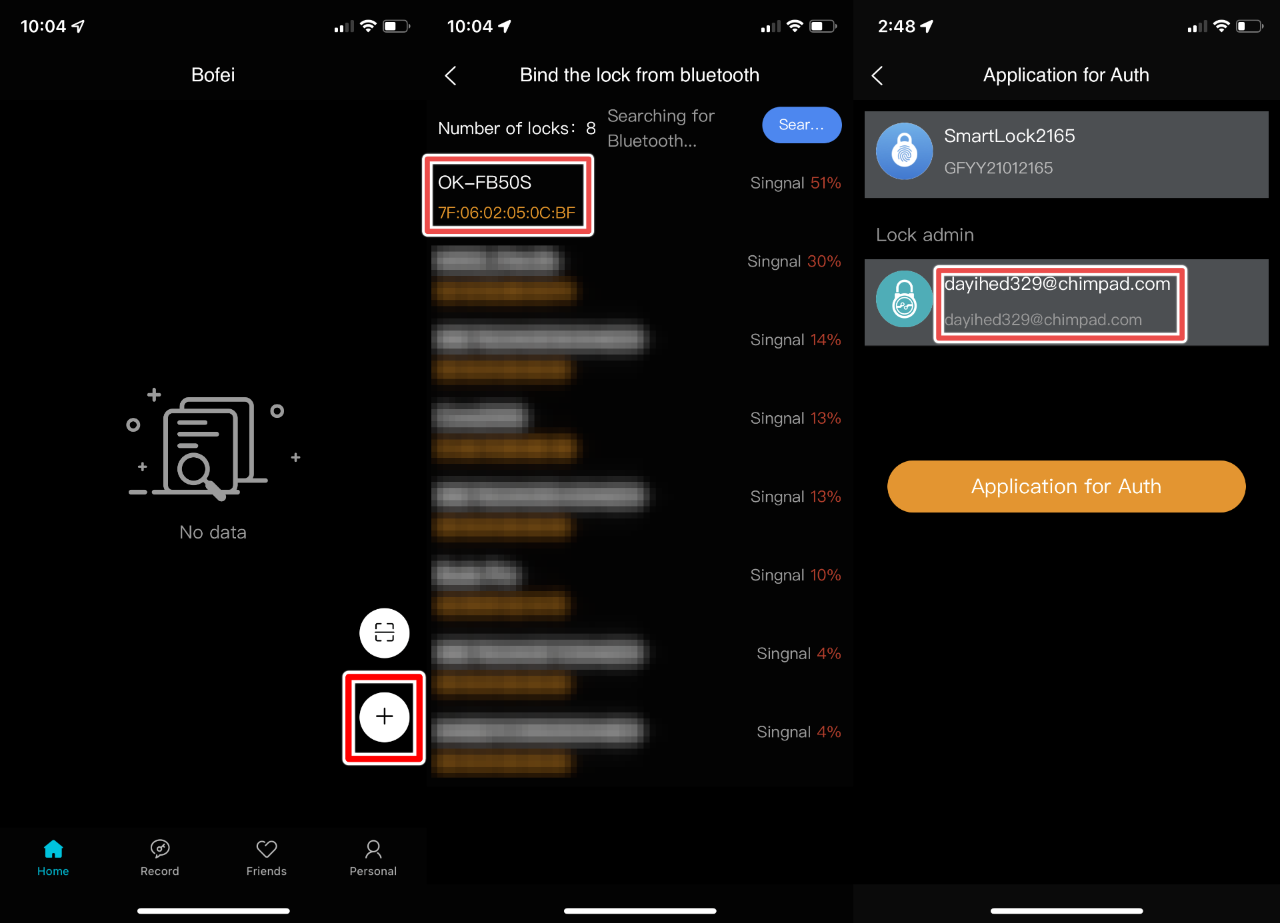
To demonstrate an attacker's ability to expose the email or phone number associated with a Megafeis smart lock owner's account, the following steps can be performed within version 1.4.2 of the DBD+ application:
- Log in to the DBD+ application using a valid account.
- Once authenticated, press the "Add" button.
- Once a device advertising its Megafeis model number is discovered, tap on it.
- If the lock is already bound to a user, the resulting permission request will expose its owner's login username.
The screenshots below illustrate these steps from the view of the mobile application and reveal the username/email address of a test user researchers created while investigating this issue: