Insecure Password Policy & Lack of Rate Limiting on Megafeis Smart Lock API Server
CVE-2022-45635
Description
The Megafeis API server had an insufficient password policy for its user accounts. This would facilitate an attacker's efforts to obtain user passwords via password guessing attacks. Additionally, the API server did not appear to have a rate-limiting function in place, increasing the likelihood of a successful password brute force attack against the server.
As described in CVE-2022-45634, an attacker within bluetooth proximity of a targeted lock could easily obtain a user's email address or phone number, which were values used in the lock management application's login process. Were an attacker to gain access to a user's password, they could take control of all locks belonging to the compromised account.
As of this advisory's publishing date, there has been no response from the manufacturer, nor is WithSecure aware of any remedial action taken
Additional information on this issue, along with related issues discovered by the researcher, can be found in the following locations:
- The Megafeis-palm: Exploiting Vulnerabilities to Open Bluetooth SmartLocks publication
- The associated GitHub repository: https://github.com/WithSecureLabs/megafeis-palm
Technical Details
The Megafeis API server allowed users to create passwords which were as short as 4 characters long and did not enforce the inclusion of special characters, numbers, or upper-case letters. The screenshot below shows the application's guidelines for passwords:
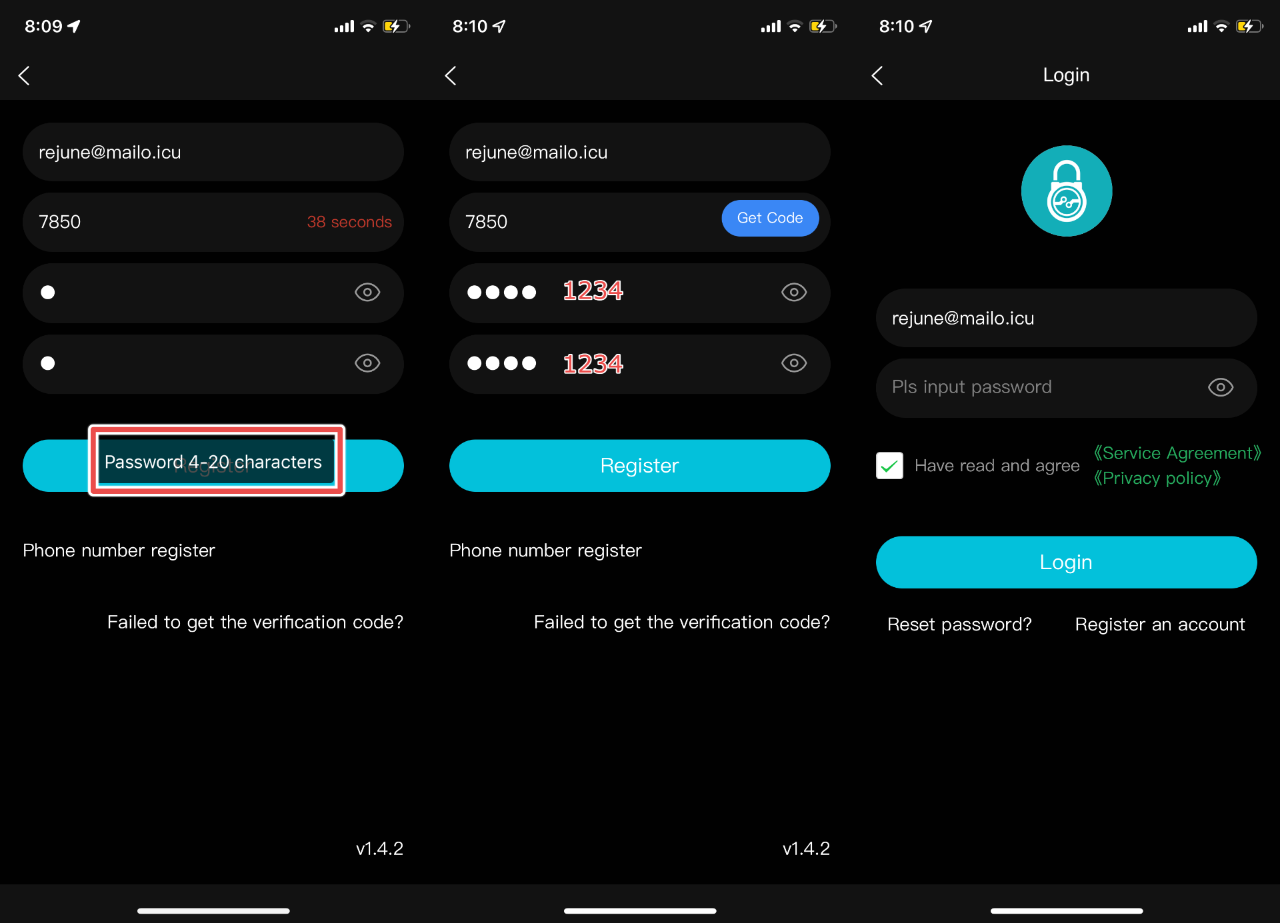
The API server did not appear to have a rate-limiting function in place, increasing the likelihood of a successful password brute force attack against the server. To demonstrate this, WithSecure created a script which attempted to brute force passwords against its own account.
The following screenshot shows shortened console output from the script displaying 50 consecutive attempts at correctly guessing a test user's password:
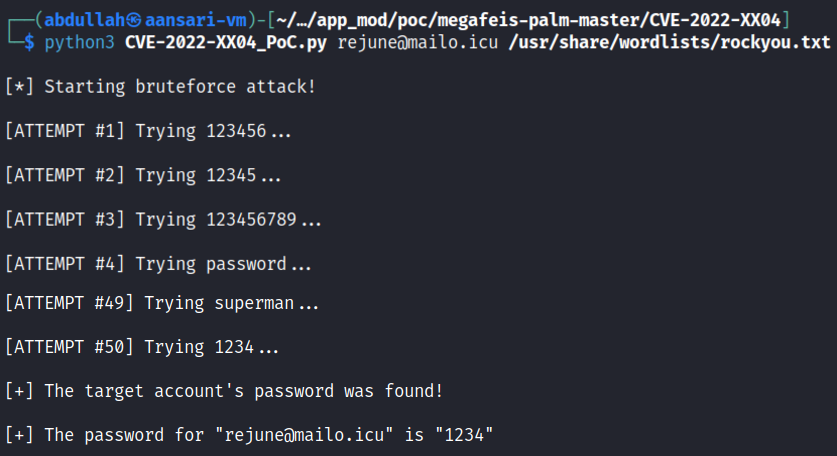
Proof of Concept
WithSecure created a PoC script that can be used to fully exploit this issue and compromise a legitimate DBD+ user's account via online password guessing. This would allow an attacker to gain access to the targeted user's account and all of their connected smartlocks. The script requires the target smartlock owner's username and a wordlist of candidate passwords.
The script is available here: https://github.com/WithSecureLabs/megafeis-palm/blob/main/CVE-2022-45635/CVE-2022-45635_PoC.py