Screen Capture via UI Overlays in MediaProjection
CVE-2018-9524
Description
Google introduced the MediaProjection service to the Android Framework in Android 5.0. This gave Android application developers the ability to capture screen contents and/or record system audio. Prior to android 5.0 application developers required their applications to run with root privileges or sign their applications with the device’s release keys in order to use system protected permissions to capture screen contents.
With MediaProjection, application developers no longer need a root privileges nor do they require to sign their applications with the device’s release keys. Furthermore, there are no permissions that are required to be declared in the AndroidManifest.xml in order to use the MediaProjection service.
To use the MediaProjection service, an application would simply have to request access to this system Service via an Intent. Access to this system Service is granted by displaying a SystemUI pop-up that warns the user that the requesting application would like to capture the user’s screen.
It was discovered that an attacker could overlay this SystemUI pop-up which warns the user that the contents of their screen would be captured, with an arbitrary message to trick the user into granting the attacker’s application the ability to capture the user’s screen.
Impact
This vulnerability would allow an attacker to capture the user’s screen should the user tap of the SystemUI pop-up that has been overlayed by the attacker with an arbitrary message.
The lack of specific android permissions to use this API makes it harder to determine if an application uses the MediaProjection service.
This vulnerability is particularly severe since the SystemUI pop-up is launched within the context of the attacker’s application making it possible for an attacker to detect the pop-up and draw an overlay without the user noticing.
Cause
The primary cause of this vulnerability is due to the fact that affected Android versions are unable to detect a partially obscured SystemUI pop-ups. This allows an attacker to craft an application to draw an overlay over the SystemUI pop-up which would lead to the elevation of the application’s privileges that would allow it to capture the user’s screen.
Furthermore, the SystemUI pop-up is the only access control mechanism available that prevents the abuse of the MediaProjection service. An attacker could trivially bypass this mechanism by using tapjacking this pop-up using publicly known methods to grant their applications the ability to capture the user’s screen.
Interim Workaround
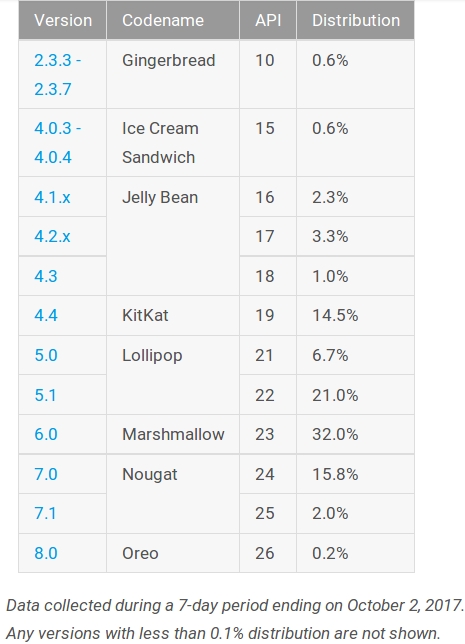
This vulnerability has currently only been patched in Android 8.0. However, due to the issue of version fragmentation within the Android ecosystem there are a number of Android devices that can’t upgrade to Android 8.0 or no longer receive updates from device vendors that would still be vulnerable. According to the Android developer dashboard as of 02-Oct-17, approximately 77.5% of active android devices are still vulnerable to this particular attack[1].
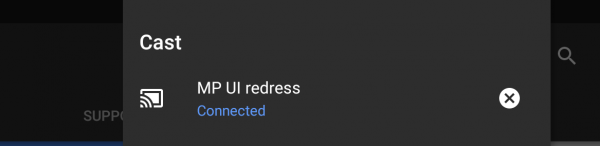
However, this attack is not entirely undetectable. When an application gains access to the MediaProjection Service, it generates a Virtual Display which activates the screencast icon in the notification bar. Should users see a screencast icon in their devices notification bar, they should investigate the application/process currently running on their devices. An example of which is shown below:
Solution
This vulnerability has been addressed in Android 8.0 and Android users are advised to update to Android 8.0. Google has released a patch for older devices and as such users are recommended to update their Android devices.
Android application developers can defend against this attack by enabling the FLAG_SECURE layout parameter via the application's WindowManager. This would ensure that the content of the applications windows are treated as secure, preventing it from appearing in screenshots or from being viewed on non-secure displays.
Technical details
Please refer to the attached advisory and complementary blog post.