Athena
Introduction
Athena is developed in C# using the .NET framework. The key aim of the tool is to provide investigators and other security professionals with a streamlined way to create structured threat information from raw IOC data collected during an investigation.
Athena works with the concept of an “Incident”. The user inputs the basic information about their incident such as its name, key dates and a short description. The user can then add “Indicators” to this investigation. An indicator is a distinct piece of intelligence and the currently supported pieces of information are:
- Domain
- IP address
- File information (Name, hashes etc.)
- Registry key information
One or more observables can be linked together using “Relationships”. There are numerous types of relationship, which are described using a “Verb” derived from the STIX definitions. These verbs are descriptions such as “Downloaded From”, “Dropped By” etc. and allow context to be added to indicators with ease.
Observables can be created via the Graphical User Interface (GUI) or via the import of a Comma Separated Value (CSV) spreadsheet. The use of a CSV to import into Athena can dramatically cut down the time taken for an investigator to formalise their IOC data during or after an investigation.
Once the investigator has entered their incident information, created or loaded their indicators and linked them together using relationships – they are able to export the data to one of the supported formats.
Currently, the supported formats for export are:
- STIX 1.1 XML
- MISP JSON (MISP version tested on 2.4.7.6)
Athena also saves to a proprietary format to allow later retrieval, manipulation and re-export of IOC data to additional formats. There are currently no plans to support to reading STIX or MISP file formats due to the complexity and size of these formats.
Usage Overview
After selecting “File -> New”, the user should complete the fields in the “Incident Overview” section.
The user can then proceed to add Indicators to their incident using the “Add Observable” button or the “CSV Import” button.
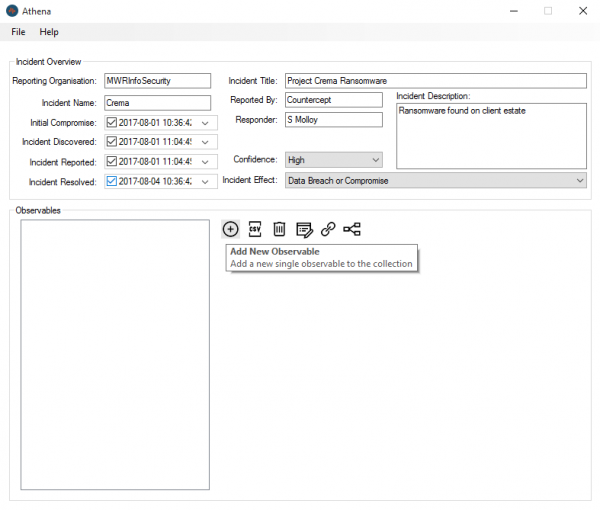
The “Add Observable” window allows the user to enter information manually, by selecting the “Indictor Type” and populating the fields. For Malware Samples, hashes can automatically be generated.
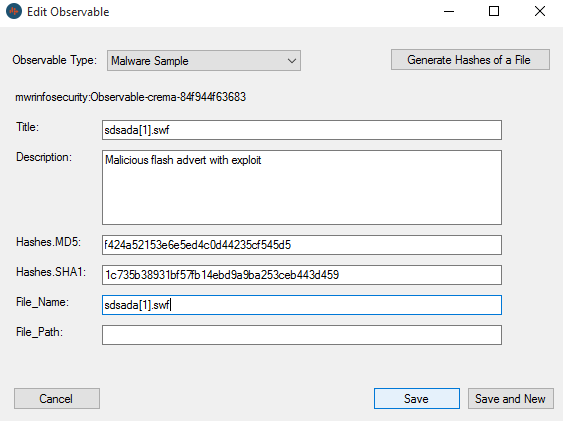
Relationships can then be built using the “Add a Relationship” window. This allows multiple Indicators to be linked together with a descriptive verb.
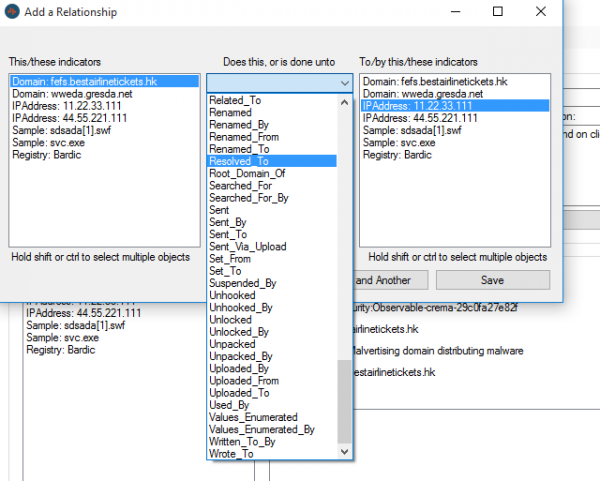
Once observables have been added and relationships created, the collection can be visualised using the “Visualise Data” window. This feature is still in development and is only intended to allow a sanity check of the entered information.
When the investigator is happy with the collection they have created, it can be saved to the native format and then exported to the desired Threat Intel format using the “File -> Export...” menu.
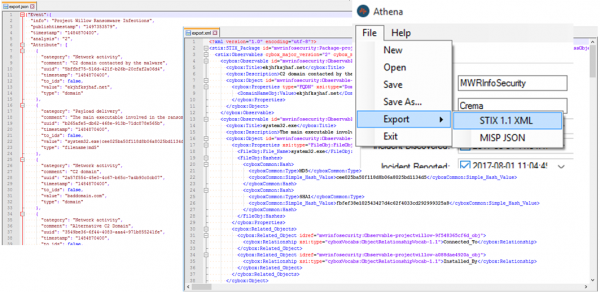
All Athena functionality is documented in greater detail in the user guide which can be located on the GitHub alongside the source code.
Roadmap
There are many features we would like to include in the Athena program:
Short term
- Usability and stability improvements
- Additional export formats (STIX 2.0)
- More flexible and customisable relationship vocabulary
- Code implementation to encompass STIX “TTP”
Medium Term
- Direct Integration with other systems for direct submission of IOC data
- Improvements to IOC import functionality to ease mass import
Credits
Athena was originally developed by Steve Molloy, Senior Incident Response Consultant at MWR InfoSecurity.