Email-Delivered RMM: Abusing PDFs for Silent Initial Access
by Jeremy Ong
30/07/2025
Introduction
Since November 2024, WithSecure has been tracking a slight uptick of targeted activities leveraging Remote Monitoring and Management (RMM) tools embedded within PDF documents. The activity primarily targets organizations in France and Luxembourg, using socially engineered emails to deliver a clean PDF containing an embedded link to an RMM installer, a simple but effective method of bypassing many email and malware defences.
RMM tools, while legitimate in nature, have emerged as a popular initial access and persistence vector for threat actors. Their use enables attackers to gain access to the networks, disable security features, escalate privileges, and deploy subsequent malware using a “clean” and trusted tool. This tactic is neither new nor uncommon; notably, the Black Basta ransomware group has been observed impersonating IT support personnel to trick victims into installing RMM tools, which were then used to deliver ransomware.
The purpose of this blog is to highlight the risks posed by such tooling, and provide awareness and insights into the ongoing, trending activity with an emphasis of the evolution of the RMM tools used by threat actors.
Activity Overview
The activity observed and tracked by WithSecure since November 2024 represents a highly focused pattern, primarily targeting organizations in France and Luxembourg. The threat actors leverage carefully crafted PDFs tailored to the victim’s industry while also referencing the specific RMM tool being deployed. These PDFs are often disguised to look like invoices, contracts, or property listings to enhance credibility and lure victims into clicking the embedded link. For instance, one PDF used to target a real estate organization in the Netherlands was written in Dutch and included blurred images of properties. This design was intended to create the illusion of legitimate content that has been obscured, prompting the victim to install a program. In this case, the program was FleetDeck RMM.
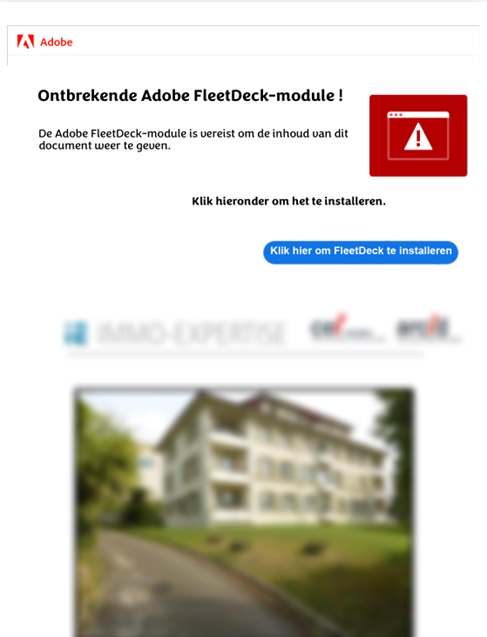 Figure 1. PDF used for targeting a real estate organization in Netherlands
Figure 1. PDF used for targeting a real estate organization in Netherlands
While the majority of observed activity has focused on France and Luxembourg, it has not been limited to these countries. Most cases have occurred within Europe, suggesting a regional targeting strategy. Moreover, the inclusion of Luxembourg as a primary target is particularly interesting. Despite its proportionately small population compared to other European countries, Luxembourg has one of the highest GDPs per capita globally, making it an appealing target for financially motivated threat actors. The activity appears to be prioritizing high-value sectors such as energy, government, banking, and construction industries, commonly targeted in cybercrime. This reinforces the idea that the threat actors are targeting organizations where a successful compromise could yield greater financial gain, rather than broad-scale distribution, which typically involves sending out high volumes of generic phishing emails in hope that a few recipients will take the bait.
Although isolated activities have also been seen outside of Europe, the overall geographic pattern supports the likelihood of a Europe-based or Europe-focused threat actor, with a strong understanding of local language and business sectors.
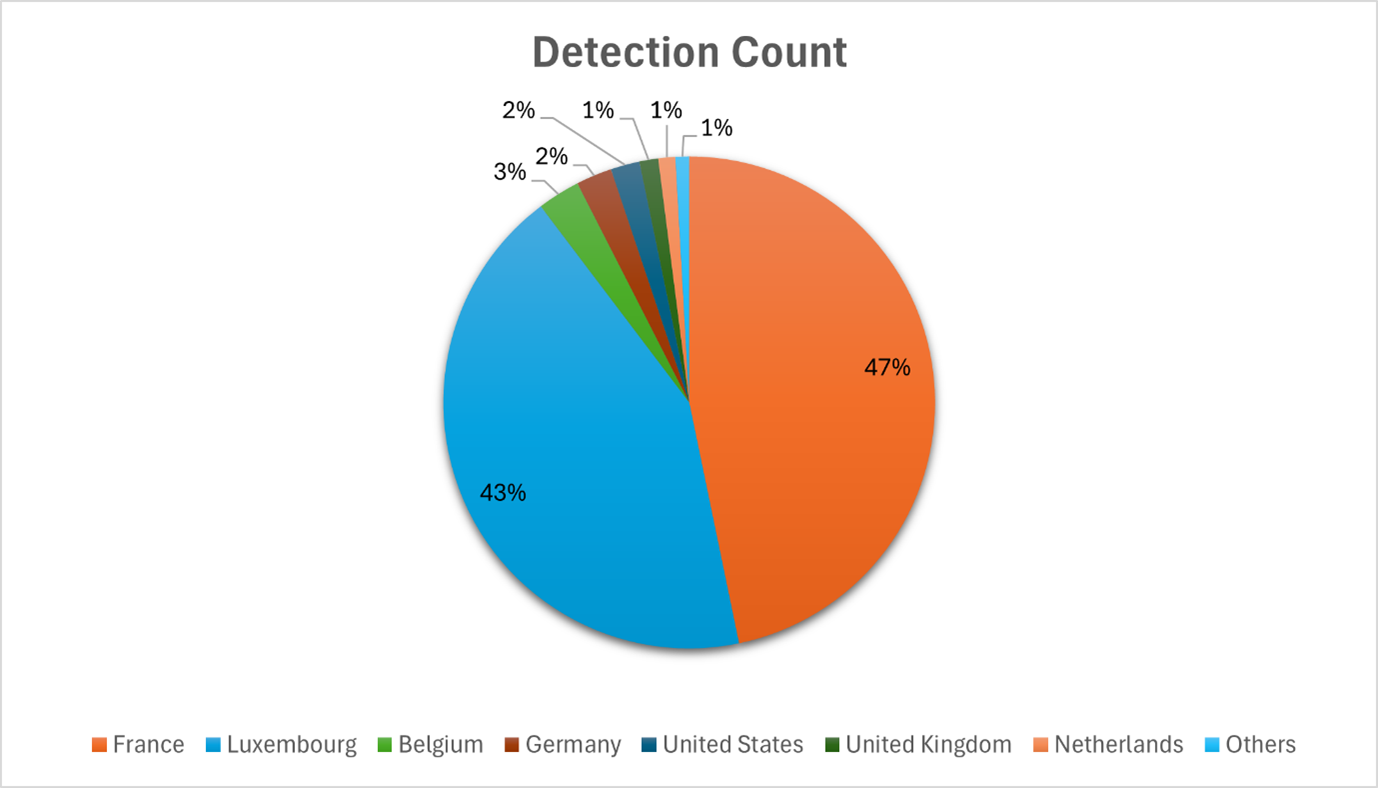 Figure 2. Detection volume of the campaign by country, November 2024 – June 2025
Figure 2. Detection volume of the campaign by country, November 2024 – June 2025
Delivery Vector
The delivery mechanism used in these activities centers around PDF documents containing a single embedded direct download link to an RMM installer. These PDFs are typically distributed via social engineering emails, crafted to appear relevant to the victim’s industry or role. To enhance credibility, the threat actor either spoofs email addresses or registers lookalike domains. In many cases these emails impersonate real employees in significant roles from the spoofed organization, further increasing their authenticity. This combination of email spoofing and impersonation tactics significantly improves the success rate of the phishing email.
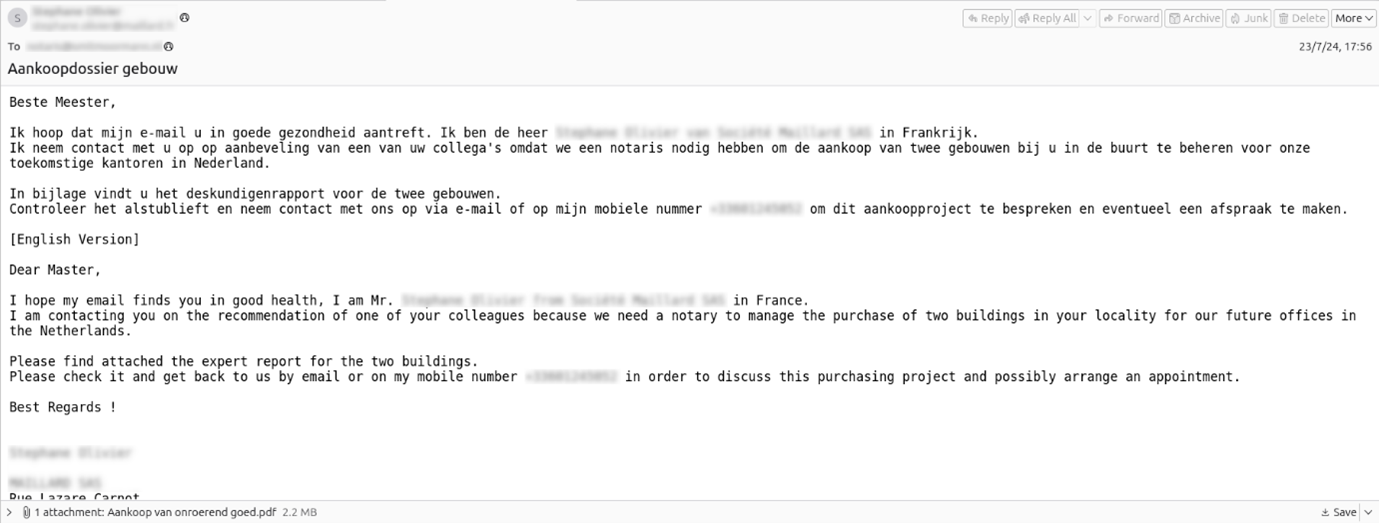 Figure 3. Social engineering email used to distribute malicious PDF
Figure 3. Social engineering email used to distribute malicious PDF
The embedded links within the PDFs point directly to download URLs generated by the RMM vendors when the threat actor registers an account on the platform. These URLs are unique and may include information such as access key, which link the installer back to the attacker’s account. Since RMM tools are commonly used for legitimate IT support, this tactic allows the attackers to bypass email and antivirus scans, not only on the email attachment itself but also on the embedded URL and the downloaded executable.
In more recent activities, a notable shift in delivery method has been the abuse of Zendesk as a distribution channel. Instead of relying solely on traditional phishing emails, the threat actor has submitted tickets or replies through Zendesk that include the malicious PDF. While the exact content of these tickets or replies remains unclear, analysis from VirusTotal indicates that the malicious PDFs were being downloaded from Zendesk hosted URLs. Although Zendesk scans attachments for malware, the embedded link within the PDF points to a clean, signed RMM installer hosted on a reputable domain, allowing them to evade detection. This shift likely reflects an effort to bypass email security controls by leveraging a trusted platform that is not typically associated with phishing delivery.
RMM Tooling
WithSecure has observed the use of several different RMM tools across the tracked activity cluster. These include well-known solutions such as FleetDeck, Atera, and Bluetrait, among others. The selection of tools does not appear to be tailored to the victim’s industry or region. Instead, the common factor among these tools is their availability via direct download links and the fact that they do not require any further setup or configuration after installation. This enables threat actors to streamline the infection process. Once the victim clicks the embedded link and runs the installer, the RMM tool becomes immediately operational and often grants remote access without requiring further user interaction or authentication steps. A notable exception to this pattern is the use of ScreenConnect, which was delivered via a redirect URL embedded in the PDF rather than a direct download link. This may have been done to avoid exposing the RMM instance domain, which appears to be visible in direct download links based on VirusTotal searches. This approach could make it more difficult for defenders to attribute or track the activity.
While WithSecure began tracking this activity in November 2024, earlier instances of RMM usage have been observed in VirusTotal submissions dating back to July 2024.
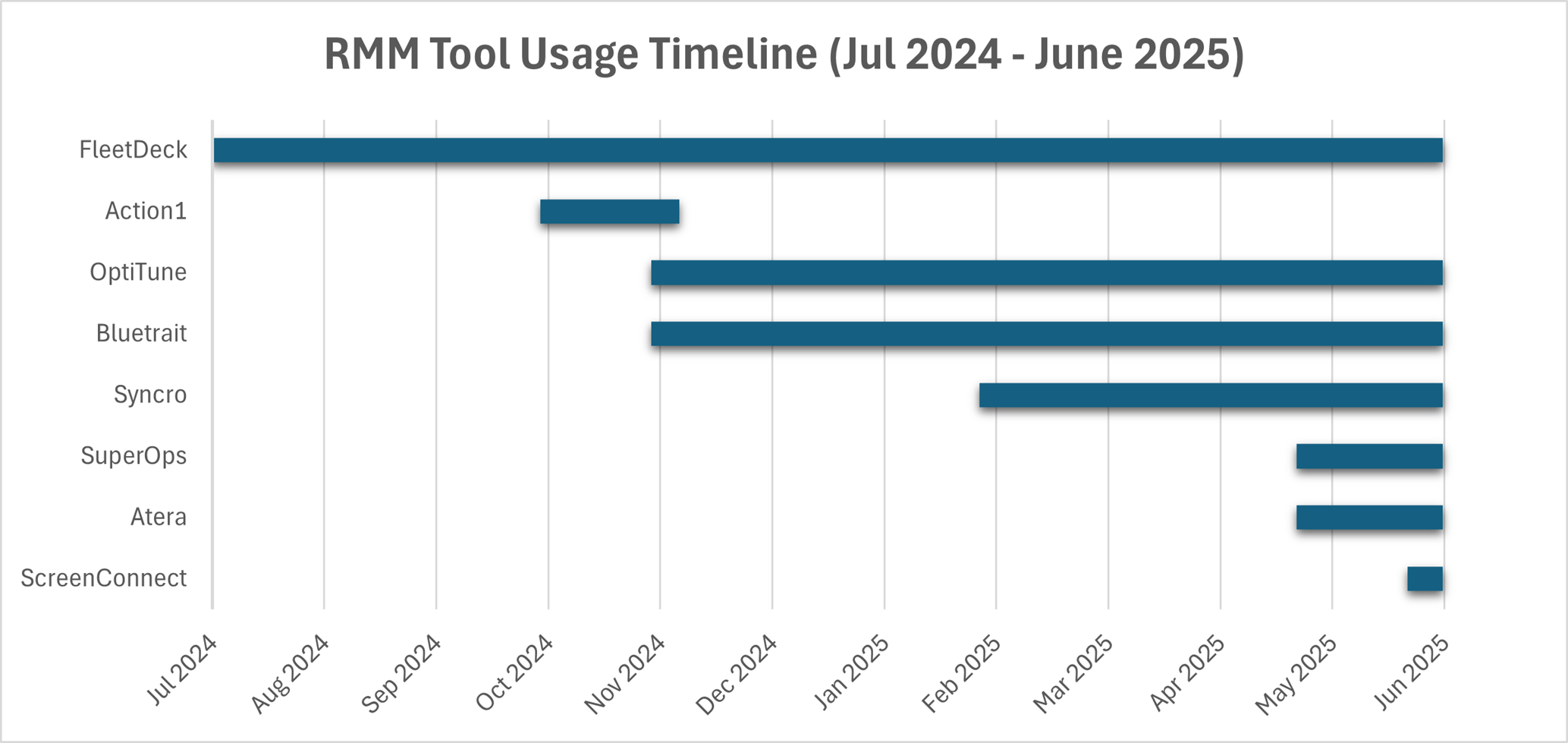 Figure 4. Timeline of RMM tool usage observed (July 2024 – June 2025)
Figure 4. Timeline of RMM tool usage observed (July 2024 – June 2025)
File metadata
Metadata analysis of the PDFs used in this activity cluster reveals notable patterns that offer insight into the tooling used during PDF creation. WithSecure has identified seven distinct values in the author metadata field:
- Dennis Block
- Guillaume Vaugeois
- Alina Georgiana Mihalcea
- WorldStream Customer
- ALEXANDERS PARAIN
- DABA DABA
- COMPTA VDB
While these names do not appear to correspond to known threat actors, and no clear linkage has been established between them, their inconsistent and seemingly random nature suggests that they may be randomly assigned. This could reflect the use of varied tools to generate the phishing documents, or an intentional effort to diversify metadata in order to evade detections.
Further metadata analysis, specifically the creator and producer fields, provides additional insight into the tools used to generate these PDFs. Several samples indicate the use of common document editing platforms, including:
- Microsoft Word
- Canva
- ILovePDF
These findings indicate the use of widely available tools in the document creation process, possibly to streamline production or obscure the origin of the files.
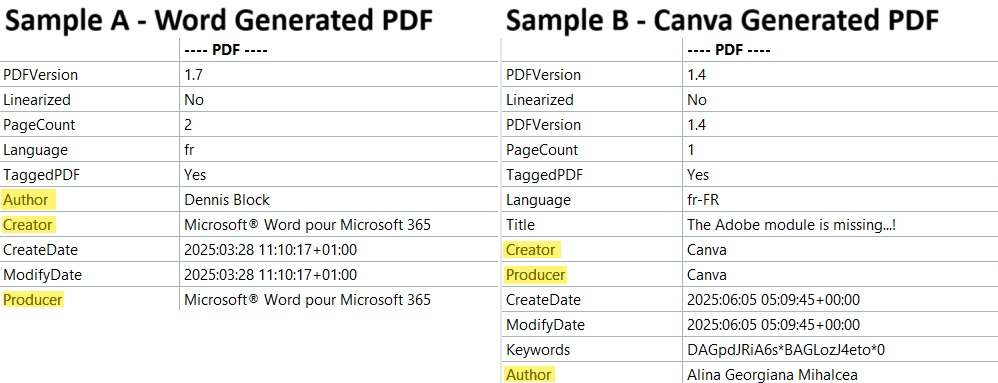 Figure 5. Metadata comparison showing different authors and creation tools across PDFs.
Figure 5. Metadata comparison showing different authors and creation tools across PDFs.
| Author | Tool (Creator/Producer) |
Dennis Block | Microsoft Word, ILovePDF |
Guillaume Vaugeois | Canva |
Alina Georgiana Mihalcea | Canva |
WorldStream Customer | Microsoft Word |
ALEXANDERS PARAIN | Canva |
DABA DABA | Canva |
COMPTA VDB | Canva |
Table 1. Summary of author metadata and PDF creation tools used in observed samples
Mitigation
To reduce exposure to this activity cluster, organizations should implement a combination of technical controls and user awareness measures. Blocking direct downloads of known RMM installers can prevent initial access, particularly when tools like FleetDeck, Atera, or ScreenConnect are not part of the approved IT stack. Furthermore, implementing application allowlisting can prevent unauthorized RMM tools from executing in the environment. Where possible, access to these installers and tools should be restricted unless explicitly required or approved by the IT or security team.
In parallel, organizations should monitor for unauthorized RMM activity. Unusual process chains, such as a PDF opening a browser to download an RMM EXE or MSI file, should trigger alerts. Endpoint detection and response (EDR) solutions can help surface this behavior effectively.
Finally, user training remains a critical defense. Employees should be made aware of phishing tactics involving fake invoices, contracts, or IT support requests that attempt to trick them into installing remote access software.
Conclusion
The activity cluster observed by WithSecure highlights how legitimate tools, such as RMM software, continue to be repurposed for malicious use. By embedding direct download links within PDF documents and delivering them through social engineering techniques, threat actors can bypass traditional detection mechanisms and lower the barrier for initial compromise.
Although no post-infection payloads have been observed, the use of RMM tools strongly suggests their role as an initial access vector, potentially enabling further malicious activity. Ransomware operators in particular have favoured this approach, with groups such as Black Basta, Conti, Royal, and BlackCat previously observed using RMM tools to establish initial access before deploying ransomware payloads.
This ongoing activity targeting France, Luxembourg, and surrounding regions underscores the importance of visibility into seemingly harmless tools, especially when delivered through unconventional vectors like embedded PDF links. Organizations should remain alert to the abuse of legitimate software and continue to harden their environments against socially engineered threats.
IOCS
Observed RMM Installer URLs
RMM Tool | Download URLs |
FleetDeck | hxxps://agent[.]fleetdeck[.]io/QsoxdPZw4B9TXSgRtqBnNM?win |
hxxps://agent[.]fleetdeck[.]io/AXcsqzW86wmaHrjPNaYQTo?win | |
hxxps://agent[.]fleetdeck[.]io/Z3dBX7JqaJpCzvCWLWYw2?win | |
hxxps://agent[.]fleetdeck[.]io/HoX9E2imWqMazYqypRUuzv?win | |
hxxps://agent[.]fleetdeck[.]io/16Dj3d4Fdn8NMMfbrVSeQn?win | |
hxxps://agent[.]fleetdeck[.]io/Nhohu2abKJS6eQiQmDFcQF?win | |
hxxps://agent[.]fleetdeck[.]io/JGGvyrtLZMfchTVtuz4Kzu?win | |
hxxps://agent[.]fleetdeck[.]io/U4KA7AKnzheqApGs3H2dJb?win | |
hxxps://agent[.]fleetdeck[.]io/Cy7aGZfvLsfKEuk8rEGPWn?win | |
hxxps://agent[.]fleetdeck[.]io/T9sTRrGyhJKjM4eFfqrnWy?win | |
Action1 | hxxps://app[.]eu[.]action1[.]com/agent/7409f2b3-8fe0-11ef-8ef6-9f7ccf3fde70/Windows/agent\(My_Organization\)[.]msi |
Bluetrait | hxxps://moduleadobeu[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=8f92d3d1-ed14-41ff-ba2d-6abeeae4c492 |
hxxps://massen[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=b888df6c-4488-4146-8fd1-9292023576ad | |
hxxps://altrotech[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=3a682a3f-ffb8-4fcb-9c24-05e714de9d9a | |
hxxps://revilox[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=7258f2f8-0da3-4b38-8632-020b07a6d4e2 | |
hxxps://mitnick[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=2763d93a-3794-41bb-9a63-28c9c17e2610 | |
hxxps://lerelaisvoyages[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=7405f906-afeb-4d4c-a11f-d7cec04b2876 | |
hxxps://sogetis[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=1bc87723-0bd5-4f07-b44f-613252212666 | |
hxxps://stauffer[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=b16aeb72-bb7a-4f0e-812e-576bf15cba19 | |
hxxps://leferry[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=8d985c6f-1862-4b80-9b32-1a28880fb5c3 | |
hxxps://managerbank[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=44de3e71-9cb2-4a28-a5fd-7ac06d446284 | |
hxxps://groupe[.]bluetrait[.]io/simple/msp_download_agent?os=windows&access_key=dd90f8fb-ff32-4041-8fc3-735e0820d58d | |
OptiTune | hxxps://manage[.]opti-tune[.]com/agent/download[.]ashx?id=c6292c97-823b-4075-be7f-c703d7d4cec3 |
hxxps://manage[.]opti-tune[.]com/agent/download[.]ashx?id=fc04f3f3-282d-4e00-a1b2-4592d5847f9d | |
hxxps://manage[.]opti-tune[.]com/agent/download[.]ashx?id=441ff695-e33b-46d6-a069-91e06d6f12d8 | |
hxxps://manage[.]opti-tune[.]com/agent/download[.]ashx?id=2f821e8d-e075-4cba-ab36-af777d3a2e2e | |
hxxps://manage[.]opti-tune[.]com/agent/download[.]ashx?id=35144ffd-cb78-45ed-84a1-154043cc954c | |
hxxps://manage[.]opti-tune[.]com/agent/download[.]ashx?id=637efb75-56a0-47a2-a4f8-b394036c753d | |
hxxps://manage[.]opti-tune[.]com/agent/download[.]ashx?id=9d5ad946-3334-479c-8d25-13573bb1f2f4 | |
Atera | hxxps://helpdesksupport1747151491046[.]servicedesk[.]atera[.]com/GetAgent/Msi/?customerId=1&integratorLogin=alexandra[.]geyer@froid-chaud-service[.]com&accountId=001Q300000TDQK9IAP |
hxxps://helpdesksupport1747151491046[.]servicedesk[.]atera[.]com/GetAgent/Windows/?cid=1&aid=001Q300000TDQK9IAP | |
Syncro | hxxps://rmm[.]syncromsp[.]com/dl/msi/djEtMzMyOTI3NTMtMTc3MjU3OTUxMi03MjgxNC00Mjc0NTk1 |
hxxps://rmm[.]syncromsp[.]com/dl/msi/djEtMzMyNjAzOTUtMTc3MTk2NDc2OS03Mjc1Mi00MjYxNzg3 | |
hxxps://rmm[.]syncromsp[.]com/dl/msi/djEtMzM0MTY5ODItMTc3NTA2ODg2My03MzAwNS00MzIxODQ3 | |
hxxps://rmm[.]syncromsp[.]com/dl/msi/djEtMzMzNTU3NTItMTc3Mzg3NjIyMi03Mjk1NS00MzA3MzY5 | |
hxxps://rmm[.]syncromsp[.]com/dl/msi/djEtMzMyNzY0NTMtMTc3MjE1MTI1MS03Mjc4MC00MjY5Mjcy | |
hxxps://rmm[.]syncromsp[.]com/dl/msi/djEtMzM1NTAwOTYtMTc3NzUzOTk0MC03MzMyNC00MzgxMjU3 | |
hxxps://rmm[.]syncromsp[.]com/dl/msi/djEtMzM1NDk5ODYtMTc3NzUzNDk5OC03MzMwMy00MzgxMjMw | |
hxxps://rmm[.]syncromsp[.]com/dl/msi/djEtMzM1NDI2NjktMTc3NzI3MDM0My03MzMwMy00MzU1MzA4 | |
SuperOps | hxxps://eu-superops-wininstaller-prod[.]s3[.]eu-central-1[.]amazonaws[.]com/agent/4046068187223527424/UQN7GX1C1UDC_19SYPURD17668_windows_x64[.]msi |
ScreenConnect | hxxps://www[.]hpgas8[.]top/Bin/secure[.]ClientSetup[.]msi?e=Access&y=Guest
|
Observed PDF Delivery URLs via Zendesk
Link | PDF SHA256 |
| hxxps://ttsonline[.]zendesk[.]com/attachments/token/LkWkQiX9tZyPCn51DKqQv2gn6/?name=RECORDATORIO+IMPORTANTE[.]pdf | a8dc8dd2f71366010a74a0e31e21d86a29a418cfc8f7574ce290bb4009417da0 |
hxxps://ttsonline[.]zendesk[.]com/attachments/token/nBdmgrkjycttoqwSzIwj0MSvR/?name=Comisiones+de+la+primera+cuota+se+requiere+actuar+en+caso+de+discrepancia[.]pdf | 4e392ea104f83c5d154c12f59200755cb8e3cdfaf058000ad24a1896cbb66fa4
|
Observed Email and PDF Attachment Hashes
Email SHA256 | PDF SHA256 |
79228809577bf65c75d8e2190f40a7201a6ea3c06521017107206ac82d8c47d5 | 9ca4fcd50376d5cdfe86c9274305720b68b9ebadf59acb97f402810f3fcd2fc3 |
e0ef73289dd4981c3f6a0d8640ea74c6cdb7340129749b44f9dc935bc56fdc33 | b1dae73270361e3f4ff7b7441dbe55fc433d6035285f2617f2b267d31de8e9c6 |
c025cd3ebd280c88d5e54ce98ff92f6085c064f971e0b01310513939113e95d0 | bb3c78a381e5288ed314a0f0a74333cf3e581f908c84d82d997da4ab37f95141 |
3f480d98a3d7d793152be1393e74c8d7ebbce67c94a6ca968b292389422e7f12 | 16b2a07c2b5a1eb7a2aeea007910d0d30819e1f80d40ee3fb304098c6be1e584 |
021f995ee8c497810ec3eecda6f87ed30ecb42ba7f22d32856b1efa231ae274b | 745663e1832367c54e1cca6bc34e73ff28e45caa794dc8c104045d71ba8a63f8
|
Observed PDF Hashes and Author Metadata
Author | PDF SHA256 |
Dennis Block | 8905f6c6f08c4530bc97ec51def19272d9df344b46ad2186265fb77d0db2003c |
035f491059caf1402e6d3886ab405b61ab8a7b8d5937fb4c5a25484c1a6b6db4 | |
3268341dc59e2486672e22c8645046098b6280ad89d4a872ef98e649e2c5cd07 | |
f317ebdb581fc8accf00ede9c1eab756ecb966a02bca149a66ca080a9e62aaf5 | |
ae4375eec439b0ee87f01fab2af55dcc5b663d7bc4ed6cd7da3c5c659e7a66fe | |
e9727ab064f38171090ad232533e8c8dd0cc4d56d57ec7bb05b5320b3ad25221 | |
e09524690e24198c1cd5808954ec0e35e09febc9527ae1036be91db605f05faf | |
ddb96adab43c3c626494bca98b00c31e8d2d4be81139f438a1b6bb98cd21db65 | |
0d8d1243844659f2b7eb7f0c7bec3057c05a0e3731f8330112b6d04dad718528 | |
65878589cff87634b9f16abd0839c89020ac70499ffce8719c5a06ac40f3be1c | |
9395edd13d1d71f64b49503fb1c04836bcbb16b9bfe2b3744d4d53f49aa08385 | |
b17cd37ad6d3adc89b84c7468730eda8702791531939f421880d605ef556ebf0 | |
51159f622351a896439f605349301395c84cb68c245230ec76767e906d295391 | |
6a9fa47a7f48274558cee2e0b901d2adaa1d97016899ed1b4c2f628760c35a0a | |
d19f13124449b4d89028e80579174a3d00cd10e0e28c3dd287b36ff50a5f3d0a | |
a6d75e175a3ceac0750eac4e2481dc260551218b61a3e19b9c8c1af4667a9913 | |
1fd8c22a0bda1df277545700ac42183447ee3657f5106c9fccee623978a5b594 | |
0771ddbaa101bbf4c051702026f56206bedf1b17e6dad7e68880edce2e63bbb8 | |
a086433cd40c2c44fb76d29698333ffddac950e9dc9c7735cd9bf45194de496c | |
7f47f0b9d53927f05933d4881210023c876014f84515238a9e2abfb3b9bb28f3 | |
e694758dc5495d71092ea50a8226400d38a18095e6936e063038c65374949016 | |
c2325214fcd3ec4990a6caff5eb920f30296ad7ed2c9c753e5815f83fc447304 | |
0d7b4a1d4558e0c6d29bc9a83f20db350f5afe6666942a372ec9a97003365a2d | |
1904d3ea755e13f64cb09f372cd9b107883f76ca73149d4f21f97022fdb28afe | |
c6a8637397a3570c0f153be98303e6b7492c3dac3b94976f6fb2408f46a1763d | |
87d3d71acd6aaf23626e63a95b0f33c0f3fe953456db39fbaa64c61fb9cedaff | |
9dd3d568196bc8f1e417f743422fc017f48554e4604dd670b3ff06d6bf80b957 | |
Guillaume Vaugeois | 0875b075f3a9da3d345e0a2b922a134baa0cbf2eaf5754da2a75d2dab2341d13 |
6950bd0c815b0ff60404610274380621d38a3e3a22c2e72d7c64f6adeb06c187 | |
81e3329a89f839952ff0ffbc9cd3e3c80796115184e9b5a0bccba99d806d8b61 | |
871d457b03ec654bfb15e568cfb630198aca3b92be86b4e2684c2a09be983563 | |
e9ba9b7e78607ca072e7cab9890c1742a7f2d82b8a6a6da2c56ac9732dfc9bd9 | |
0c76e50d3cc947d17990c3afd44295c6299430942a4eccb1c87f8b3ea4d2def8 | |
22e64e7ec0056a4bbeeab7acb3d46ef796c5256c9c934369ad29c35a1df050eb | |
1bcfbc79c000a18721dfbe1fa44906389146ba9e1c940f8ebe61c5ab5658e4bd | |
c8f077a306b2a960713c374ceb82210eb78975f62c0c5aa1dbb22e36faf949db | |
Alina Georgiana Mihalcea | 129df778cde4bb19049d9f48bfaaabf7baec541072dd64c0024b55d63e793a9f |
| f0119123b86550df9ec2d7946030aab7d387aef37d006eb352498b374c0df941 |
1f146f8fe2e7eb5d0dd0a6b7b92259bae51c0fcb376e039743ec591ba8d01e22 | |
dc129f059e6d58e1f38e0eed886a5fb165c069a8028a4c7debea1d8a028e0231 | |
2048c6d87ad991d2975b07568bdd5ef52e210f27b7ac85506e37619096c4f0ff | |
0e63cc926ac72c4e65eba76f06cbfaabe95623701432c5fe67d1fe00663fba9d | |
a3e89e90ef69385aa3dfabfa76c7fdfad28063ed6032a4439dfef48694ed487e | |
eea65f23c944c5104ec7ee55e4939b51babeddcdbb52459fc2b065434e07e30d | |
e87c3fb7031ac89ce8f38b9542c55bf96097faea50d7887a731e466bc9b6f990 | |
0c8c4b93170a8de7c857c5f4030c6a1e2394940bbd3d48f100014b3d0c64ed90 | |
WorldStream Customer | 3182309746d206db5eadb8743160bf802e012ea70dfa5ee39120e0494532098f |
c9beb4996ad6ade7070e684c7d3f6f8e8d02de30af0bfaf85504ab06a36d7c76 | |
7e10d37f2abb2bbdf1c4f7bf29277cf01a385301682068a82006563445f80a20 | |
44baab4692375ad15363acdec3f57eb7cfea0e65456fff921624e6a531089aac | |
ALEXANDERS PARAIN | 951ceed3102757d284e84804c4aa002a22502ab72fef10d2317be5192ae8a0ee |
52d3d7ae7c8f53249867714f24bafe68aeae665a5fa7cd4b426bb3e637d9cbf0 | |
DABA DABA | d3211a41eb9bc727b6de76fe9262ffdf4f38f6c8ca8a6e10d3b82a6be5c07564 |
COMPTA VDB | 9ca4fcd50376d5cdfe86c9274305720b68b9ebadf59acb97f402810f3fcd2fc3 |