DarkGate malware campaign
Executive Summary
Vietnamese cybercrime groups are using multiple different Malware as a Service (MaaS) infostealers and Remote Access Trojans (RATs) to target the digital marketing sector. These actors greatly value Facebook business accounts and hijacking these accounts appears to be one of their primary goals. The targeting and methods of these groups heavily overlap to an extent that suggests that they are a closely related cluster of operators/groups. It is possible to identify campaigns carried out by these groups through non-technical indicators, such as their lure topics, lure files, and associated metadata.
Introduction
WithSecure Detection and Response Team (DRT) detected and identified multiple DarkGate malware infection attempts against WithSecure Managed Detection and Response (MDR) customers in the UK, US, and India. It rapidly became apparent that the lure documents and targeting were very similar to recent DuckTail infostealer campaigns, and it was possible to pivot through opensource data from the DarkGate campaign to multiple other infostealers which are very likely being used by the same actor/group.
The overlap of tools and campaigns is very likely due to the effects of a cybercrime marketplace and ecosystem described in the WithSecure Professionalization of Cybercrime report. Threat actors are able to acquire and use multiple different tools for the same purpose, and all they have to do is come up with targets, campaigns, and lures. As such, if you were to track their activity purely by a tool they are using you would see only a subset of their activity. Because multiple actors are purchasing and using the same tools, you could also end up tracking different actors who are also using the same tool. As such, by tracking an actor through characteristics other than the specific tool they used last, it is possible to identify a wider cross section of that specific actor’s operations.
Key findings
Multiple groupings of Vietnamese threat actors are running Infostealer campaigns using Malware as a Service (MaaS)/Commodity Malwares, targeting specific sectors/groups.
This report focuses on a group who use the same or very similar lures and delivery methods to deliver a variety of infostealer malware including:
- DarkGate
- Ducktail
- Lobshot
- Redline stealer
Either the risk appetite or technical ability of this group has resulted in them using files which have very identifiable metadata, such as:
- LNK File metadata, containing the Drive ID of the device the file was created on.
- PDFs created using the Canva design service/tool, tagged with an author UID and additional metadata.
- MSI files created using an unlicensed version of EXEMSI, which inserts a licensing message into the MSI file metadata.
Campaign and lure analysis
There have been multiple reports in Q3 2023 about DarkGate, the closely related Ducktail campaigns, and the Vietnamese threat actor cluster responsible for these campaigns. The WithSecure Intelligence report on Ducktail and Duckport is strongly recommended reading. It is a very thorough report on Ducktail, with large amounts of technical detail and observations about the tools, their evolution, and the campaigns they have been used in.
The WithSecure Intelligence report and the other open-source Ducktail and DarkGate reporting released at this time have been focused on technical analysis and functional details of the malware and campaigns. This has presented an opportunity for a different threat intelligence method to be used to contribute to the body of knowledge about these actors and campaigns.
In most cases WithSecure have observed, the initial infection attempt is detected and prevented from progressing. As such, the functionality of DarkGate often doesn’t come into play. However, by identifying characteristics of DarkGate lures and campaigns we have been able to find multiple pivot points which lead into other information stealers and malware being used in very similar if not identical campaigns, and it is assessed as likely that these campaigns are performed by the same threat actor group. These overlaps can be seen as a characteristic of the evolving e-crime marketplace described in the previous WithSecure report, The Professionalization of Cybercrime.
Detection by WithSecure DRT
Initial detection
On 2023.08.04 WithSecure Managed Detection and Response identified suspicious code injection into multiple processes on a customer endpoint. Initial triage by the Detection and Response Team (DRT) identified the presence of a suspicious VBS file and the harvesting of credentials from browser databases, suggesting the presence of an infostealer infection of some type.
The activity began when a file named Salary and new products.8.4.zip was downloaded and extracted, and the contents executed. The DarkGate infection flow was the same as that previously documented in open-source reporting:
- The archive contained a VBS script which copied the legitimate windows binary curl.exe to a new location.
- Curl.exe was renamed to a random name, The renamed curl.exe was used to connect to an external destination and download two files, autoit3.exe and a compiled Autoit3 script.
- The script was executed using autoit3.exe.
- Upon execution the script de-obfuscated and constructed the DarkGate RAT from strings contained within the body of the script.
Thirty seconds after the initial install the malware attempted to uninstall the WithSecure agent from the device, although this was not successful. It isn’t possible to tell whether the uninstall attempt was an instruction from the C2 based on pre-configured logic/automation, or an automated attempt by the malware, but the speed with which this occurred after infection means it is unlikely to have been manual.
Further detections
Similar lure files and behavior were observed on two further victim organizations, though with different version numbers possibly tied to the date of creation or deployment, i.e.:
- Salary and new products.8.3
- Salary and new products.8.5
- Salary and new products.8.7
In these cases, antivirus/EDR including Sophos and Forcepoint prevented the execution of the second stage. The VBS script that downloads the second stage was recovered, and while the binary could not be retrieved from the URL in the script, the script was in VirusTotal, where it was related to the second stage binary.
Shortly after finding the binary in VirusTotal, a victim was identified where the second stage had executed, and from this device DRT were able to retrieve the initial VBS dropper script, second stage, and payload.
Interestingly, the VBS dropper retrieved from the victim contained the logic:
IF (NOT FILEEXISTS("C:\Program Files (x86)\Sophos"))THEN
It is unknown if this logic was present on the initial victim, or if it was added by the actor shortly after that wave, in response to the Sophos agent preventing execution on a number of targets.
Infection vector
Analysis of browser history on a victim device identified that the initial vector was a LinkedIn message which directed the victim to hxxps://g2[.]by/jd-Corsair, which then redirected the victim to a file hosted on Google Drive.
The initial infection vector being via a LinkedIn message is a typical method seen by WithSecure Intelligence in DuckTail campaigns, and Ducktail appears to be used by a cluster of different yet related Vietnamese threat actors.
Link to Ducktail
Very similar campaign themes and lures have been used to deliver Ducktail and DarkGate. Ducktail has been reported on previously by WithSecure and others and is almost certainly an infostealer that is employed by a cluster of actors based in Vietnam.
Differences from Ducktail
The Ducktail related DarkGate campaigns have a very similar initial infection route, but the function of the payloads differs greatly. Ducktail is a dedicated infostealer, it is in no way stealthy, and upon execution it will rapidly steal credentials and session cookies from the local device and send them back to the attacker. It has an additional Facebook Business account focused function whereby if it locates a Facebook Business account session cookie it will attempt to add the attacker to the account as an administrator, and even has functionality to automatically create and publish fraudulent ad campaigns sent by the actor to the compromised device. This additional, heavily Facebook focused functionality is still based around Infostealing, though it suggests a very tight focus for the attacker.
DarkGate however appears to be a RAT with infostealer functionality. DarkGate attempts to be stealthy, it tries to achieve persistence, it has been used for a variety of purposes, and has reportedly been used by attackers to deploy Cobalt Strike and ransomware. It very much appears that DarkGate has a much more diverse user base than Ducktail, with much more varied goals. As such however, while DarkGate is a tool which is used by and useful to multiple unrelated actors, the DarkGate behavior which most closely resembles and overlaps with the Ducktail campaigns is likely to be the same Vietnamese threat actor cluster.
Corsair campaign
The infection attempt that was initially detected used a lure that claimed to relate to the computer memory and hardware manufacturer Corsair. The URL seen during delivery of the malicious files was g2[.]by/corsair-JD. Searching for the string “corsair-JD” in VirusTotal identified multiple files that reference that URL, including a Zip, PDF, TXT, and DOCX file.
The Zip file contains the PDF, and the txt file contains instructions for downloading and opening the Zip file. This appears to be a common bundle format for the actor, though sometimes using a DOCX file instead of a PDF file.
The g2[.]by/jd-Corsair redirect has been changed by the actor over time, at one point redirecting visitors to a file hosted on Google Drive, then at another time redirecting to a file hosted on Dropbox.
The DOCX file was Job Description of Corsair..docx.
Corsair campaign instruction file
The .txt file identified was Salary and new products.txt. This plain text file contains the g2[.]by URL which directs to the Zip file, and the password for the Zip file, fbads123. The contents of the file suggests that it is sent to victims, and that the strength of the lure is expected to induce them to download and open the archive containing the malware dropper:

This Salary and new products.8.2.1.zip was at one point accessed via the g2[.]by/Corsair-JD URL and was hosted on drive[.]google.com
PDF Salary and Products.pdf was accessed via another g2[.]by URL, which redirected to a Dropbox link.
Unless intentionally scrubbed, PDF files will have metadata that can tell us more about who created the file and what they created it with. In this case, this PDF file was created by someone using the graphic design service/tool, Canva.
File metadata
Microsoft Office
Microsoft Office inserts metadata into the files it creates, as do most pieces of software. Investigating the Corsair campaign identified the file Job Description of Corsair..docx. Office files contain a lot of metadata strings, but the values of interest were:
- Creator
- LastModifiedBy
The values in these fields were both a westernized version of a Vietnamese name. While an extremely common name in Vietnam, in the VirusTotal file corpus it is not that common.
While not particularly interesting, the following metadata values from the original DOCX file can be used to narrow down the search only to files created in the same version of Microsoft word:
- Application: Microsoft Office Word
- AppVersion: 16.0
Filtering on these values and the creator name field identifies only three other files in VirusTotal:
- Job description.docx
- Job Description of Marshall.docx
- Job Description of Marshall.docx
Canva
The metadata for the Canva created PDF file named PDF Salary and Products.pdf was as follows:
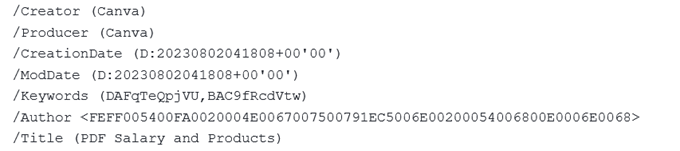
Of particular interest here is the Author UUID, which is most likely a unique reference. Searching on that UUID in VirusTotal brings up one other PDF file, “Job Description of Corsair..PDF”. This is very likely to have been created and used by the same actor, not only because of the Canva author ID, but because it has the same filename, apart from the file extension, as one of the previously identified docx files.
The PDF file metadata contains the following:
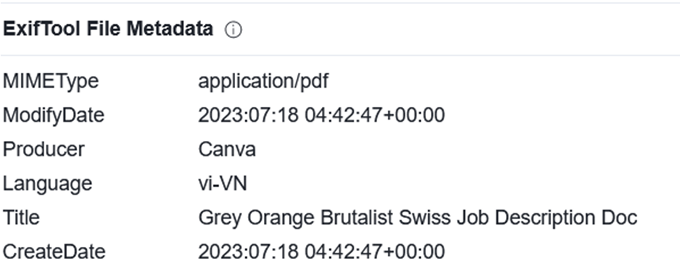
The author’s name (not the unique ID) is similar to the author of the word document. The Title “Grey Orange Brutalist Swiss Job Description Doc” is the name the file was given by the actor when it was first saved in Canva.

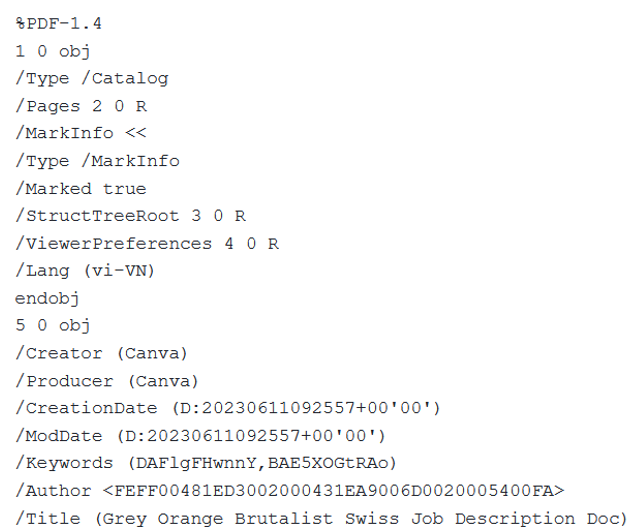
Pivoting on that title returns another Canva created file, Leader Marketing Job-Description.pdf, which has a very similar theme and content, and is most likely created by the same actor/group, although the Canva author metadata is different:
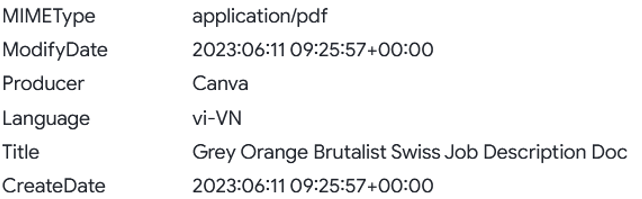
The Exif metadata also returns a different author name:
Redline stealer
Pivoting on the author ID of the Leader Marketing Job-Description.pdf file finds a Redline stealer executable named license.txt_, which contains the exact same Leader Marketing Job-Description.pdf file. License.txt_ is a Windows executable file, however it contains the PDF file within the binary, most likely as a decoy document that is dropped when the malware is executed.
Redline stealer was first reported in early 2020 as an MaaS infostealer, and has remained active since then. Some reporting has shown that it has been distributed through AutoIT scripts, as have other Infostealers, however the method of distribution in that case is very different to the DarkGate use of AutoIT, and seems rather more technically advanced. The most recent reporting on Redline stealer also seems to describe a more technically skilled campaign than the DarkGate activity that we observed, however Redline stealer is a MaaS, and so just like DarkGate there will be multiple threat actors running campaigns using the same malware in different ways.
The Redline stealer binary connects to 103.14.48[.]247:2130. There are some big giveaways amongst the communicating files for this IP address that tell us it is related to our actor, and to Redline stealer, such as the file Redline.exe.
File | Notes |
Redline.exe |
|
JOB_DESCRIPTION_ECOMMERCE_MARKETING_MANAGER.pdf |
|
Fbads.exe | Fbads123 was used as a password in the Corsair campaign. |
Makedisk |
|
JD_Digital_Marketing_Specialist.pdf | JD was used several times in the Corsair campaign |
MSI File metadata
MSI Wrapper (10.0.51.0) Metadata
The AutoIT compiled scripts used by the attacker are MSI files. Inspecting the OLE metadata for these files finds the following interesting strings, which tells us that the files were created with a specific, unregistered version of a software that wraps executable files in MSI bundles, named MSI Wrapper:
Metadata Field | Value |
application name | MSI Wrapper (10.0.51.0) |
subject | Application Verifier x64 External Package - UNREGISTERED - Wrapped using MSI Wrapper from www.exemsi |
The application name is quite rare in a search of VirusTotal file metadata, with only ~240 hits in mid-September 2023. However, of those 80 were submitted to VirusTotal in the last month, so use of this version of the tool appears to be ongoing. Just over 50% of the files have multiple detections, and a number of the undetected files are legitimate tools and executables wrapped with MSI wrapper, such as Advanced IP Scanner or Notepad++. Inspecting a random sub-set of those legitimate files finds that many have been bundled with other files that do have detections. This echoes reporting that Search Engine Optimization (SEO) ad fraud has been used to push trojanized version of Advanced IP Scanner and Notepad++, which include DarkGate or other infostealers in a bundle with the legitimate software.
"Application Verifier x64 External Package - UNREGISTERED - Wrapped using MSI Wrapper from www.exemsi"
In addition to the version application and version number appearing in the application name field, it appears that when the software is not registered it will also put the following message stating that in the Subject field:
"Application Verifier x64 External Package - UNREGISTERED - Wrapped using MSI Wrapper from www.exemsi"
Looking for this finds far fewer hits in VirusTotal, 88 at time of writing.
Use of an unregistered version of this MSI wrapper does not mean that a file is malicious, however it does appear that many of the submitted files are compiled AutoIT scripts that have been converted to MSI files. It is likely that one or several actors are using this unregistered software as part of the malicious build pipeline. It may even be supplied with or built into whatever DarkGate builder the MaaS supplier is selling.
Whatever the reason, use of this unregistered MSI wrapper appears to be a strong signature for Infostealer related activity with multiple lure themes and delivery methods, such as malvertising and download squatting, as reported elsewhere.
Investigating the IP addresses, domains and URLs that these MSI files were either hosted on, or contain references to, identifies some benign domains and a number of suspicious locations. The benign domains appear to be due to the legitimate executables used as lures. Many of the malicious locations use the same uncommon high ports as the original malicious C2 IP:
Suspicious URLs associated with MSI files wrapped with unregistered version of MSI Wrapper |
/no_halt_7891.msi |
/no_sec_no_startup51.msi |
/persist.msi |
/wzxfh |
/wzxfh |
/startup_persist_no_halt2840.msi |
/ais_to_sign.msi |
/error_no_decoy_2840.msi |
/all_enabled_vm_enabled7891.msi |
/ais_binded_moderate_halt_vm_enabled_2840.msi |
/files/twitter.msi |
/no_halt_opts_enabled.msi |
The URLs are interesting, the 4-digit numbers are the same as the port numbers seen in use on the suspicious DarkGate related hosts. Combined with the text, it appears that these are mostly descriptive names for the MSI files.
Suspicious IPs associated with MSI files wrapped with unregistered version of MSI Wrapper |
hxxp://80.66.88[.]145:7891/ |
hxxp://80.66.88[.]145:9999/ |
hxxp://162.243.71[.]6/no_halt_7891.msi |
hxxp://162.243.71[.]6/no_sec_no_startup51.msi |
hxxp://162.243.71[.]6/persist.msi |
hxxp://162.243.71[.]6/startup_persist_no_halt2840.msi |
hxxp://80.66.88[.]145:2840/ |
hxxp://162.243.71[.]6/ais_to_sign.msi |
hxxp://80.66.88[.]145:2351/ |
hxxp://80.66.88[.]145:2841/ |
hxxp://162.243.71[.]6/error_no_decoy_2840.msi |
hxxp://162.243.71[.]6/all_enabled_vm_enabled7891.msi |
hxxp://162.243.71[.]6/ais_binded_moderate_halt_vm_enabled_2840.msi |
hxxp://5.34.178[.]21:2351/ |
hxxp://5.34.178[.]21:81/files/twitter.msi |
hxxp://5.34.178[.]21:9999/ |
hxxp://149.248.0[.]82:2351/ |
hxxp://149.248.0[.]82:9999/ |
hxxp://162.243.71[.]6/no_halt_opts_enabled.msi |
hxxp://179.60.149[.]3:9999/ |
hxxp://179.60.149[.]3:2351/ |
hxxp://185.143.223[.]64:2351/ |
The IP addresses linked to these MSI files includes the original C2 IP in the original incident investigated by WithSecure, 149.248.0[.]82.
Suspicious Domains associated with MSI files wrapped with unregistered version of MSI Wrapper |
hxxp://sanibroadbandcommunicton.duckdns[.]org:5864/ |
hxxp://sanibroadbandcommunicton.duckdns[.]org:9999/ |
hxxps://alianzasuma[.]com/wzxfh |
hxxp://alianzasuma[.]com/wzxfh |
Only two domains were identified in this way, though they include a duckdns[.]org subdomain, which is a very commonly abused dynamic DNS provider.
Drive serial number and device id in LNK Files
LNK files include a variety of metadata if not scrubbed by the creator. Many LNK creation tools do not add this metadata or falsify it. Talos have written an informative blog post on the subject of LNK files and LNK file creation tools.
The metadata includes the Machine ID, which is simply the hostname of the creating device, and also the drive serial number field. The hostname is not always that useful, however while the Drive ID is not universally unique, it is long enough to identify the disk drive that the LNK file was originally created on with only a low chance of collision. As such it associates LNK files created on the same disk/device. If you are lucky and the actor has not been careful, the drive serial number of an LNK file can be a good way to identify other LNK files created on the same disk drive.
There are a number of LNK files in VirusTotal which execute commands to connect to DarkGate C2 servers, and some of these files have the same Drive ID field, indicating they were created on the same device/hard drive.
All of the LNK files in the below table connect to hxxp://5.188.87[.]58:2351/ and download an MSI file.
Some of the LNK files have compressed parent files (i.e., archives they were extracted from) which give us more information about the lure being used.
SHA256 Hash | Filename | Compressed Parents |
2c6af12f603743fcc3effdc24783c969c906816960fbfbf012974fc04722a679 | C:\Users\user\AppData\Local\Temp\kk2ykypd.4v2\2.jpeg.lnk | LostItems_Pictures_ARCHIVE.zip |
e0d1b1b166ba025c918335b3733d908bb89ecbce776ee273941bfa38acbba765 | C:\Users\user\AppData\Local\Temp\kk2ykypd.4v2\1.jpeg.lnk | LostItems_Pictures_ARCHIVE.zip |
e877f6398a85e428256352d6a82f4219eed939404a00aaeec9a98eb35a3e518f | Repair.lnk | - |
810e332e43e812aeb8aabca6bd0d00b693d20cbb61f486be28ce1287a337a4fa | C:\Users\user\AppData\Local\Temp\u14xjkhe.ep0\New_KPI.pdf.lnk | New_KPI.zip |
e5b8de9d983f635947c25183efc9b490cf185388634cf937426e3cd1235b250e | Vacation Schedule Change 2023.lnk | - |
ed362c7417996deec5ba3b2f41e0b0f907d701aea8b403cf3fa4050cbe3a21b6 | C:\Users\user\AppData\Local\Temp\3szh1m2z.g5v\Repair.lnk | Repair.zip |
86717824da845b1537fb24583dd9825be1ea8e032d3f5758357d1da615e82567 | - | Presentation of the new project. August 2023.rar |
12b5711ace38966a9a6767fc331f835a3ee5b68d0f901aabf2c5d069d46f7b44 | - | Presentation of the new project. 22.08.2023.rar |
These LNK files all have the exact same creation time, 2021.01.09 03:03:06 +00:00.
Looking at these LNK files it became obvious that most of them could be located by searching for LNK files which contain the strings “cmd.exe”, “curl”, and “Show Minimized No Activate”. This turns out to be a very reliable way to search for malicious LNK files in general, presently returning over 100 LNK files in VirusTotal, each with multiple detections. Some of the files found by this method were yet more files using the same filenames, version number format and behaviour as this actor.
G2[.]by URL shortener
This is a Vietnamese URL shortener service and is likely to be more heavily used by people in Vietnam. Many URLs are short random strings with a similar format, but some include specific strings that tie back into the Corsair lure DarkGate campaign, or to similar campaigns that use different organisations as lures.
URL | Notes | Redirects to |
Corsair-jdfbadsnew | fbads123 was used as a password on the corsair campaign malicious zip files | hxxps://docs.google[.]com |
PDF-salary |
| hxxps://dl.dropboxusercontent[.]com/[…]/PDF-Salary-and-Products.pdf?[…] |
Corsair |
| hxxps://dl.dropboxusercontent[.]com/[…]/New-products-and-detailed-project-information.18-7.zip?[…] |
Jd-corsair | Referred to by Job Description of Corsair..docx | - |
Corsair-jd |
| hxxps://docs.google[.]com |
Marshall | Refers to Marshall amps | hxxps://docs.google[.]com |
Marshall-salary-15-9 | Note appended version number, commonly seen in campaigns | - |
Marshall-salary-16-9 |
| hxxps://drive.google[.]com |
1V3B |
| Job details the position - the policy - the salary - and the projects by TTH AGENCY.docx.rar Public.boxcloud[.]com apisdata[.]xyz |
H37n |
| 1. Outdoor Voices Fashion - Digital Marketing Projcect.scr Hxxps://onedrive.live[.]com |
F2v2 adJt | Links to archive containing Ducktail executables | https://dl.dropboxusercontent.com/[...]/Job%20description%2031.4.zip?dl=0 |
Lures and themes
Job description archive files
While at first glance “job description*.zip” may seem a weak identifier, it appears that very few legitimate job descriptions are distributed as zip files, and it is likely that even fewer are then uploaded to Virustotal. In fact, this theme and specific file format are relatively strong identifiers for malicious file bundles that are characteristic of this actor cluster.
Searching for files with this name identifies multiple zip files that contain Ducktail infostealer binaries with fashion brand lures such as Prada and Ralph Lauren, and also zip files using the Indian finance company Groww as a lure.
SHA256 Hash | Filename |
a959814cc4017c5c14969addb80c6967c8ad20650896005e4dd22d5dc54da614 | Job description_salary_policy_marketing products_new_list_2023.zip |
876ec4b014e5779d81af67d04fbb50ccfd965dcb8ea3283cdcb3817e8543c593 | Job Description Plan - KITON Brand 2023 (1).zip |
d80213cf11a387d8a443c022a8e46e1c881f319c966113a2d3cc565af665ca2c | Job description - Groww.zip |
cfc2a67960e2195ec06fc923122bf4a4ce6f4c734801914b1ff250abb564b398 | $RVTH800.zip |
f7cdbc96f1841f378706d0d609b29999d202801403807c23ac89c63224314d09 | Job Description Prada Group 2023.zip |
2f2f9dc5b8dcce5c9f1261b8d693218017cf348240284820359cd8e86794b282 | Job Description - Ralph Lauren 2023.zip |
There are multiple zip files named Job Description – Groww.zip which are password protected, however Groww is a relatively uncommon string in the filenames of files submitted to VirusTotal. Searching on this identifies additional zip files with slightly different lures such as Groww Development Documentation.13-7.zip, and an accompanying VBS file, Groww Development Documentation.13-7.vbs. As well as the familiar bundle and filename format, this VBS file also connects to the original Corsair campaign C2 address, hxxp://149.248.0[.]82:2351/
C2 Infrastructure
The original C2 IP address of the Corsair campaign, hxxp://149.248.0[.]82:2351/, has been associated with a number of files from many different campaigns in VirusTotal. Many of the files appear to be paired, i.e.:
hxxp://149.248.0[.]82:2351/msiyfucokvo | hxxp://149.248.0[.]82:2351/yfucokvo |
Filename of files that contact hxxp://149.248.0[.]82: |
04f4a0c40bc6c16441a1ca4c6.exe |
2.vbs.vir |
C:\Users\user\AppData\Local\Temp\fsvauHMM.msi |
C:\Users\user\AppData\Local\Temp\WfMTTQFAPCohE.msi |
C:\Users\user\AppData\Local\Temp\xzhgnxpf.vbs |
C:\Windows\Installer\598646.msi |
Details of the project.vbs |
f5561472c4dfbfd7314c1c287683afd5.virus |
Groww Development Documentation.13-7.vbs |
Job description new.vbs |
Job description...vbs |
Job Description.vbs |
Job Description.vbs |
Job description.vbs |
Job Description.vbs |
Job description.vbs |
Job Description123.vbs |
Online job description.lnk |
OppyVYah.exe |
sussy.msi |
test.bat |
Z- Detailed salary sheet and commission 23.8.1.vbs |
Z- Detailed salary sheet and commission 29.8.vbs |
Z- Detailed salary sheet and commission 30.8.1.vbs |
Z- Detailed salary sheet and commission.vbs |
Z- Detailed salary sheet and commission10.8.vbs |
Z- Detailed salary sheet and commission11.8.1.vbs |
Z- Detailed salary sheet and commission11.8.vbs |
Z- Detailed salary sheet and commission14.8.1.vbs |
Z- Detailed salary sheet and commission15.8.1.vbs |
Z- Detailed salary sheet and commission17.8.vbs |
Z- Detailed salary sheet and commission8.7.1.vbs |
Z- Detailed salary sheet and commission8.7.vbs |
Z-Salary and detailed project..vbs |
Z-Salary and detailed project..vbs |
Z-Salary and detailed project.vbs |
Lobshot malware
Among the files that communicate with this C2 IP is OppyVYah.exe (a5cccdf086c63bea47a509c683e7b4214d1a2be0522fc835788887117e92d41a), which is identified as Lobshot, a malware with remote access capabilities.
Identified C2 Ips
While a large number of files were identified as associated with these malicious campaigns, they communicate with a relatively small number of C2 servers.
C2 Servers |
117.0.194[.]195 |
144.76.111[.]91- alianzasuma[.]com (Noisy but hosted malicious files) |
149.248.0[.]82 |
158.160.81[.]26 |
162.243.71[.]6 |
167.114.199[.]65 |
178.33.94[.]35 - sanibroadbandcommunicton.duckdns[.]org – DCRat server |
179.60.149[.]3 |
185.141.60[.]18 |
185.143.223[.]64 |
46.173.215[.]132 |
5.188.87[.]58 |
5.34.178[.]21 |
66.42.63[.]27 |
80.66.88[.]145 |
82.117.252[.]140 |
89.248.193[.]66 |
94.228.169[.]123 |
94.228.169[.]143 |
Common ports open on these IP addresses are:
- 2351
- 9999
- 2841
- 7891
- 5864
- 2840
The most common of these is port 2351, and a search for URLs on this port returns over 400 URLs. A random subset of these were inspected and all were identified as DarkGate related.
IOCs
IP Addresses |
117.0.194[.]195 |
149.248.0[.]82 |
158.160.81[.]26 |
162.243.71[.]6 |
167.114.199[.]65 |
178.33.94[.]35 |
179.60.149[.]3 |
185.141.60[.]18 |
185.143.223[.]64 |
46.173.215[.]132 |
5.188.87[.]58 |
5.34.178[.]21 |
66.42.63[.]27 |
80.66.88[.]145 |
82.117.252[.]140 |
89.248.193[.]66 |
94.228.169[.]123 |
94.228.169[.]143 |
Domains |
Alianzasuma[.]com – Noisy but hosted malicious files |
sanibroadbandcommunicton.duckdns[.]org |
Passwords |
fbads123 |
fbadsnew |
URLs |
:2351/msi* |
:2351/* |
LNK Metadata |
Drive serial number: 10DA-4067 |
Machine ID: win-r3rim0p93dd |
MSI File metadata |
Subject: "Application Verifier x64 External Package - UNREGISTERED - Wrapped using MSI Wrapper from www.exemsi" |
Application name: MSI Wrapper (10.0.51.0) |
Dropper archive names |
"*salary*.zip" |
"*job description*.zip” |