Insecure Password Reset Code Expiry Mechanism for Megafeis Smart Locks
CVE-2022-45637
Description
An insecure expiry mechanism for password reset codes was discovered in how Megafeis-branded smartlocks handled password reset requests. An unauthenticated user can utilize this vulnerability to hijack legitimate accounts, which can give the attacking user complete unlock access to all the smart locks bound to the compromised account while simultaneously causing a denial-of-service scenario for the legitimate user.
As of this advisory's publishing date, there has been no response from the manufacturer, nor is WithSecure aware of any remedial action taken.
Additional information on this issue, along with related issues discovered by the researcher, can be found in the following locations:
- The Megafeis-palm: Exploiting Vulnerabilities to Open Bluetooth SmartLocks publication
- The associated GitHub repository: https://github.com/WithSecureLabs/megafeis-palm
Technical Details
When reseting a user's password via the DBD+ application, the user receives a password reset code via SMS from Megafeis. Per version 1.4.2 of the application, the password reset code is supposed to expire after 60 seconds. An example of this is shown below:
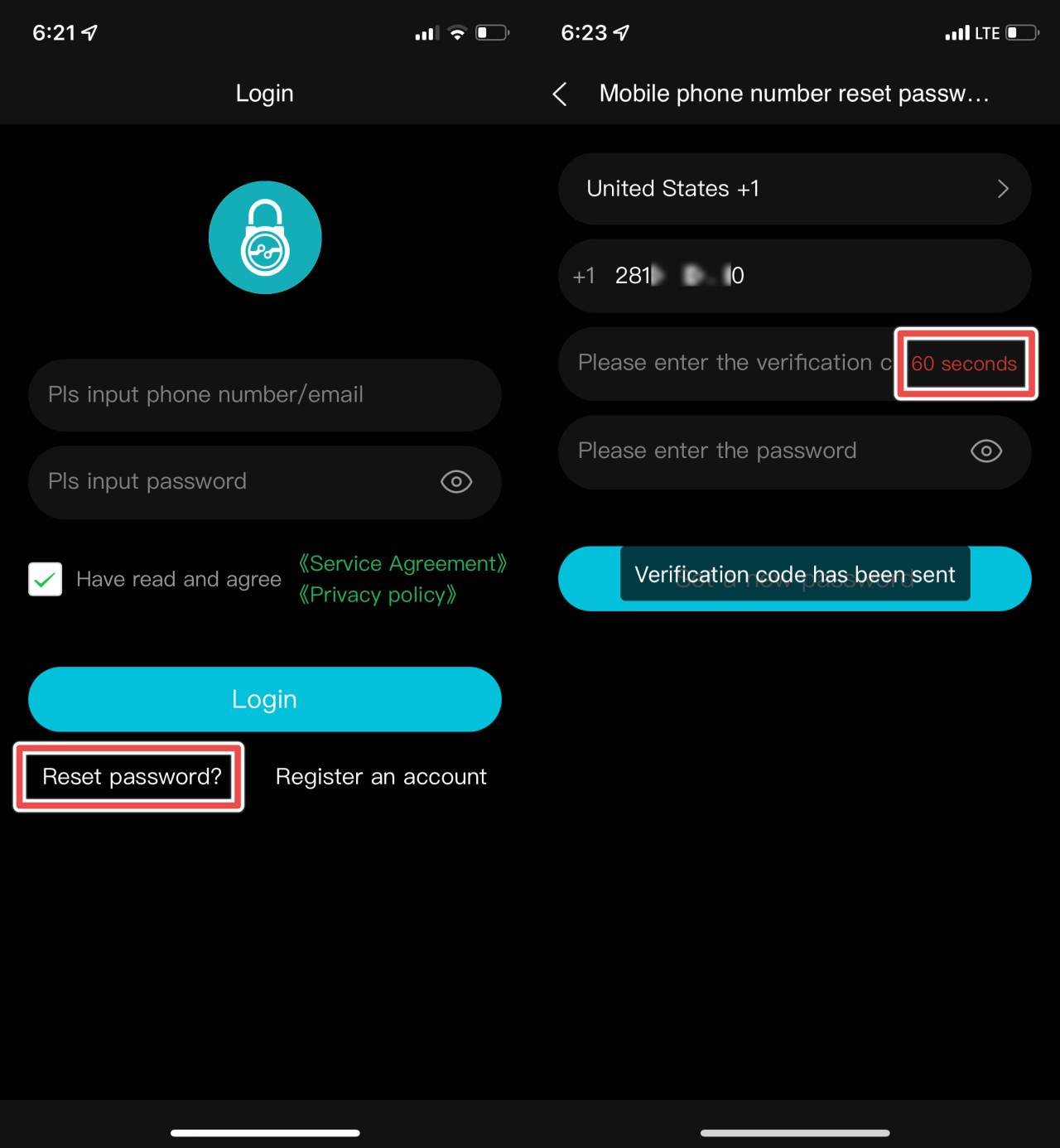
It was found that the server still accepted the password reset code well after 60 seconds. In the above screenshots, the code was sent to WithSecure at 6:21. The below screenshots show WithSecure submitting the verification code at 6:30, with the new password being accepted.
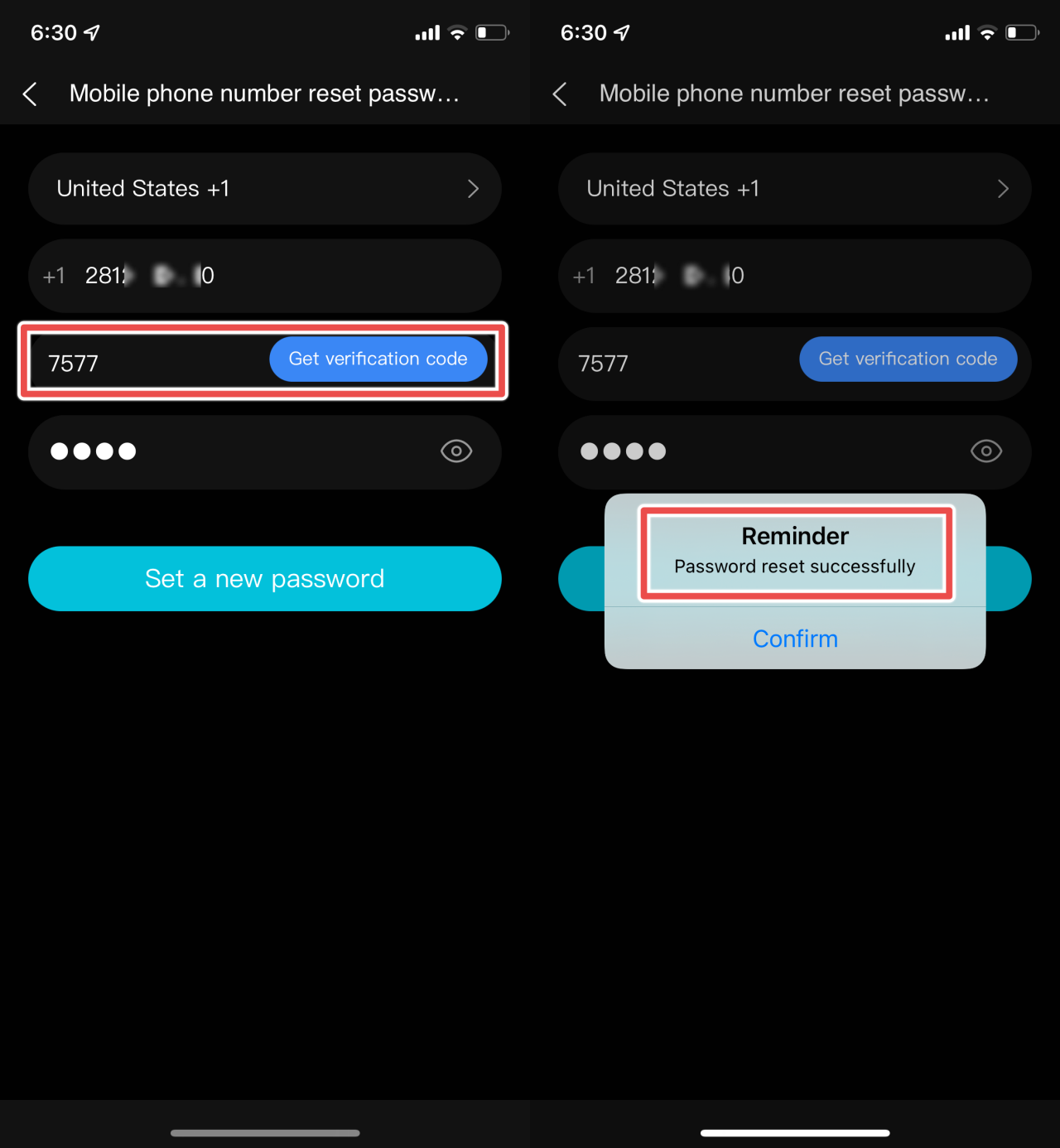
It was also found that the server did not implement a rate limiting function when making password reset requests. This opened up an attack scenario where an attacker could brute force password reset codes after making a password reset request against a target user.
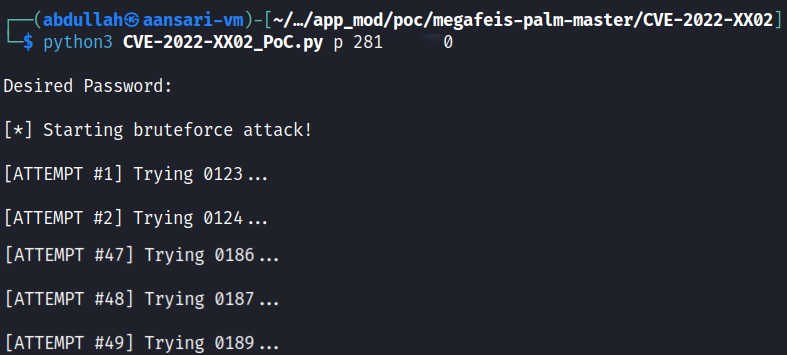
To demonstrate this, WithSecure created a script which brute forced password reset codes. The screenshot below shows shortened console output from the script, displaying 48 consecutive attempts at correctly guessing a test user's password reset code:
Proof of Concept
WithSecure created a PoC script that can be used to fully exploit this issue and hijack a legitimate DBD+ user's account, thereby gaining access to all the smart locks connected to that account. The script requires the target smart lock owner's username and the desired value to which the password should be changed.
The script is available here: https://github.com/WithSecureLabs/megafeis-palm/blob/main/CVE-2022-45637/CVE-2022-45637_PoC.py