AutoCad .NET Deserialisation Vulnerability
CVE-2019-7361
Description
The Action Macro functionality of AutoDesk’s AutoCad software suite is vulnerable to code execution due to improper validation of user input passed to a deserialization call.
AutoCad provides the ability to automate a set of tasks by recording the user performing those tasks and replaying them later. This functionality is called Action Macros. Before playing an Action Macro, the list of actions performed are presented to the user, as shown in the next figure.
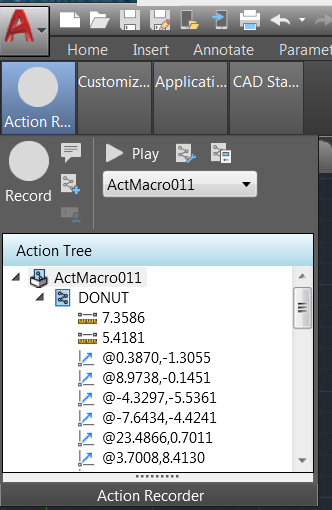
This recording will create a number of “DONUT” objects within the current drawing.
Once an Action Macro has been recorded, it is saved to the user’s “Actions” directory as a .actm file. A snippet of the underlying data of the Action Macro file for the above recording is shown below:
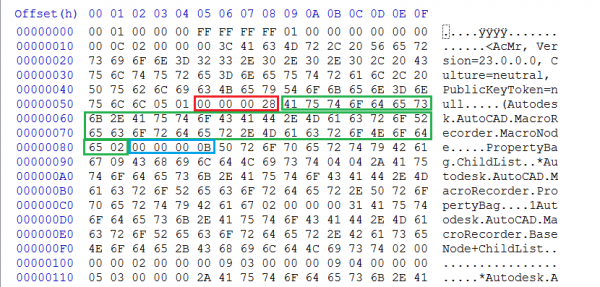
This data is made up of a number of .NET serialized objects. Highlighted in red is the length of the first object (of type AutoDesk.AutoCad.MacroRecorder.MacroNode). The green outline highlights the actual object, and the blue is the beginning of the next object.
It should be noted that this data is deserialized to allow the user to view the tree of actions within a recording prior to the user clicking “play”. The vulnerability ultimately lies in AcMR.dll, specifically the method AutoDesk.AutoCad.MacroRecorder.BaseNode.Load:
public static INode Load(Stream stream)
{
if (!DebugUtil.Verify(stream != null))
return (INode) null;
object obj = MacroManager.Formatter.Deserialize(stream); (2)
if (DebugUtil.Verify(obj is INode)) (3)
return obj as INode;
return (INode) null;
}
public void Save(Stream stream)
{
if (!DebugUtil.Verify(stream != null))
return;
MacroManager.Formatter.Serialize(stream, (object) this); (1)
}
- At (1) the object is saved using MacroManager.Formatter’s Serialize method – this occurs when an Action Macro is saved.
- At (2), the user input stream is Deserialized prior to being checked as a valid Inode object at (3). These actions occur when the Action Macro is loaded into memory.
The MacroManager.Formatter.Deserialize method is a wrapper to the .NET BinaryFormatter function:
public static IFormatter Formatter
{
get
{
if (MacroManager.m_formatter == null)
{
MacroManager.m_formatter = (IFormatter) new BinaryFormatter();
MacroManager.m_formatter.Binder = (SerializationBinder) new MacroManager.TypeRedirectionBinder();
}
return MacroManager.m_formatter;
}
}
A malicious user is able to gain code execution by replacing legitimate serialized objects in an Action Macro file. As a proof of concept, the ysoserial.net tool was used to generate a series of .NET gadgets that, when deserialised, would cause a calculator to be opened.
The command used for this proof of concept was:
ysoserial.exe -o raw -g TypeConfuseDelegate -c "calc.exe" -f BinaryFormatter > poc_calc_action_macro.actm
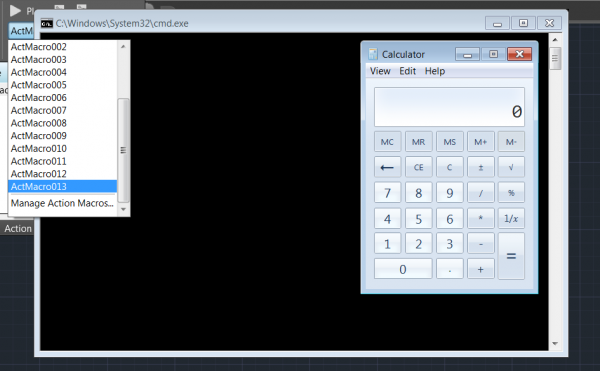
Code execution occurs when a user attempts to view the actions within an Action Macro, this occurs directly prior to replaying it, as demonstrated in the next figure. Note that the Action Macro is never “played”.
Impact
This vulnerability is of medium risk to end users. Code execution occurs in the context of the current user, no extra privileges are gained.
The potential attack vector could be through phishing of end users, whereby they are coerced into playing malicious Action Macros believing them to be legitimate. The most likely scenario could involve a malicious actor sharing an ActionMacro file online that supposedly solves a community problem.
Solution
As of February 1st 2019 AutoDesk have released a patch migitating this vulnerability. Users are advised to update AutoCad to the most recent version available.
AutoDesk have also produced following advisory pertaining to this vulnerability as well as a number of others [2].
References
[1] ysoserial.net - https://github.com/pwntester/ysoserial.net/tree/master/ysoserial
[2] AutoDesk Advisory - https://www.autodesk.com/trust/security-advisories/adsk-sa-2019-0001